Account Takeover
Financial institutions constantly face a range of fraud threats.
With fraudsters employing advanced tactics like authorized payment fraud, remote access intrusions, and mobile malware, tackling account takeover (ATO) threats requires a proactive strategy. By focusing on behavior financial institutions can gain assurance that account access is being made by the rightful user, protecting the customer’s treasure and FIs reputation.
Proactive defense against account takeover.
TALK TO A FRAUD FIGHTER
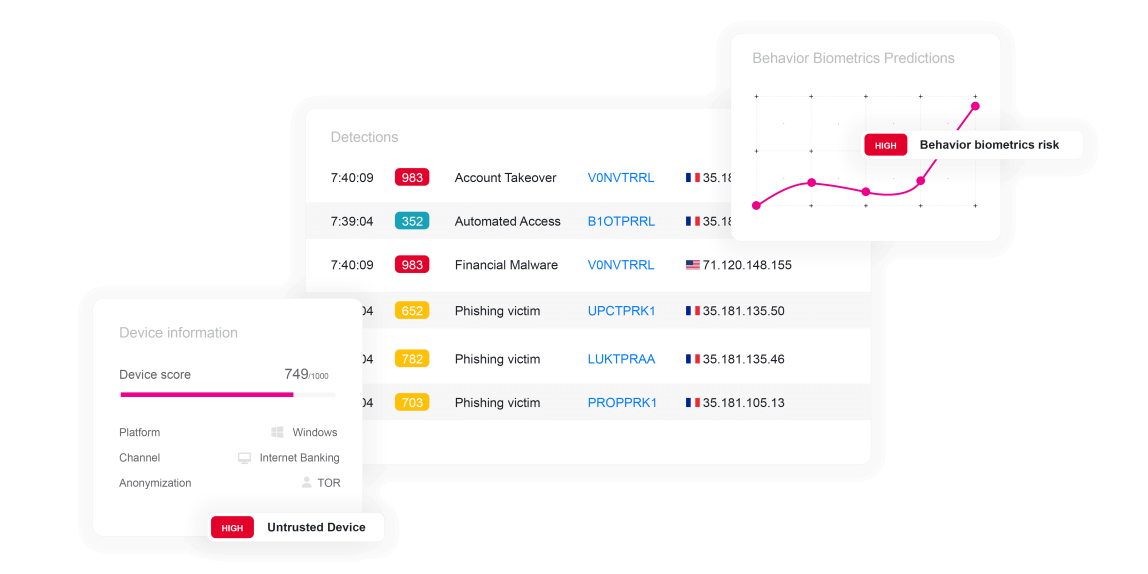
ThreatMark’s Behavioral Intelligence platform can be a critical support in a financial institution’s effort in preventing ATO threats. By analyzing patterns in customer behavior, application usage, device data, and more, ThreatMark identifies deviations from normal activity that could indicate unauthorized access.
ThreatMark’s integrated approach, combining various data points, allows for a more nuanced understanding of each customer’s digital habits. This comprehensive analysis is crucial in distinguishing legitimate activities from potential threats, reducing false positives and ensuring a seamless experience for genuine users. In the evolving landscape of digital threats, where ATO tactics are increasingly sophisticated, such a proactive and holistic approach to security is essential for safeguarding customer accounts and maintaining trust in the financial institution.
Preventing account takeover.
Types of Account Takeover threats.
-
Remote Access Scams
Remote access scams involve fraudsters posing as tech support representatives, convincing victims to grant them remote access to their devices. Exploiting fear of malware or system issues, scammers gain control to steal sensitive information, install malware, or extort money.
Learn More
-
Session Hijacking
Session stealing involves unauthorized access to an active user session. Attackers exploit vulnerabilities or use techniques like session hijacking to gain control, allowing them to impersonate the user and access sensitive information or perform malicious actions.
Learn More
-
SIM Swap
SIM swap is a fraudulent practice where attackers deceive a mobile carrier into transferring a victim's phone number to a new SIM card. This enables them to intercept calls and messages, bypass security measures, and gain unauthorized access to accounts.
Learn More
-
Financial Malware
Financial malware is malicious software designed to target financial institutions and users. It aims to steal sensitive information like login credentials, credit card details, or conduct fraudulent transactions. This type of malware poses a significant threat to online banking and financial security.
Learn More
FAQ: Account Takeover
-
How should financial institutions mitigate ATO?
Mitigating Account Takeover requires a forward-thinking strategy should exploit various indicators as integral parts of a unified context, rather than separate layers. This approach will reveal activities and behaviors that indicate bad intent. Examples of contextual data include:
- Application
- Behavior
- Device
- Network data
-
How can ThreatMark prevent Account Takeover?
ThreatMark’ Behavioral Intelligence Platform can detect irregular login times, unusual transaction patterns, or access from unknown devices and locations. These indicators enable the system to predict fraud in real-time. Enabling financial institutions to take immediate action, ThreatMark can therefore prevent fraudulent activities before they occur.
-
SIM Swap Scams & How to Prevent Them
SIM swap scams are one of the most damaging and high-profile scams in the modern era.
Read More
-
On Mobile Banking Malware
Last week our SOC experts exposed FluBot – one of the most dangerous mobile banking malware currently in circulation.
Read More
Want to learn more about ThreatMark?
Complete our form to discover more about ThreatMark’s comprehensive approach to fraud disruption.