
Authorized Push Payment Scams
Financial institutions are grappling with the growing issue of Authorized Push Payment (APP) scams.
Undermining consumer confidence and leading to significant financial loss, these scams trick individuals into voluntarily transferring funds to fraudulent accounts while the customer believes they are engaging in a transaction with a legitimate party. Such scams result in considerable financial losses for victims and can severely impact the financial institution’s reputation. In APP fraud, the victims, under the illusion of dealing with a trustworthy entity, initiate these transactions themselves, making it challenging to detect these fraudulent payments.
Talk to a fraud fighter
The impact of APP scams.
-
3Bdollars is how much APP fraud loss is expected to climb by 2027.
-
50%of all fraud losses were APP fraud in H1 2023.
-
50:50liability to sending and receiving financial institutions is coming in 2024.
Protect customers from authorized push payment scams.
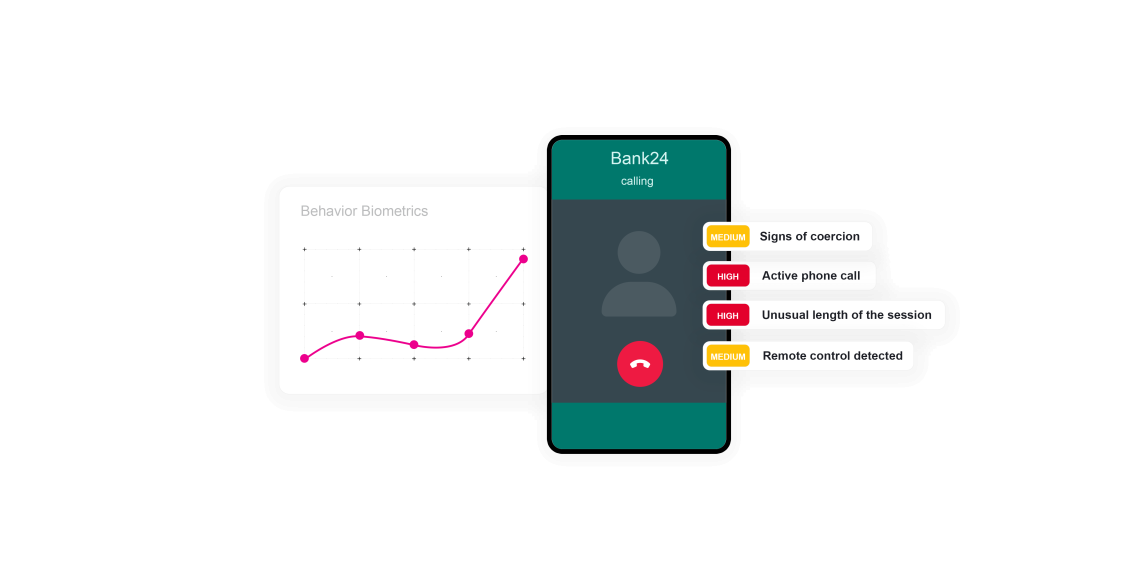
ThreatMark’s behavioral intelligence is pivotal in countering APP scams. Analyzing historical behavior patterns identifies deviations, such as unusual navigation behavior, increased session time, or unusual transfer amounts or new recipients, that can indicate potential fraud. ThreatMark’s platform also looks at device usage, such as active phone calls during a session.
ThreatMark is also crucial in autonomously stopping APP scams in real time. By continuously monitoring transaction patterns, ThreatMark can instantly identify and autonomously halt suspicious activities, such as atypical money transfers, before they are complete. This rapid response, powered by advanced algorithms, significantly reduces the window of opportunity for fraudsters, effectively safeguarding customers’ finances without the need for manual intervention. The integration of this technology ensures that banks can proactively and independently counter APP fraud, maintaining both customer trust and their financial integrity.

Mitigating APP fraud.
Understanding authorized push payment fraud.
-
Mobile Phone Call Active
Scams and social engineering exploit the weakest link in the security chain: the customer. Scammers use coercion to manipulate victims into doing something against their best interest, including moving money. One technique scammers use is calling the victim on their mobile device and talking them through the money movement process. An active call during a banking session can indicate a scam in progress.
-
Remote Access Tool in Use
When scammers have convinced an unsuspecting customer to install a remote access tool, this opens the door for the scammer to hijack a user's legitimate session. The moment the scammer starts using the tool, indicators like how the mouse is moving and how the keystrokes are received, among other behavioral patterns, reveal that a remote access tool is in use.
-
Remote Access Attacks
Legacy fraud prevention measures have limited effectiveness in detecting remote access attacks. When a session is controlled remotely by fraudsters, the bank's systems may identify the device as trusted based on its fingerprint, which may not show any signs of malware and appear to have the correct IP and geo-location.
Want to learn more about ThreatMark?
Complete our form to discover more about ThreatMark’s comprehensive approach to fraud disruption.