
Remote Access Attacks
Remote access attacks are commonly used by fraudsters to gain access to an individual’s device.
There are two methods by which remote access attacks are usually carried out: through social engineering or by exploiting vulnerabilities in software and hardware. In a scam, a fraudster convinces a victim to download a remote access tool (RAT) that allows them to take control of the device. Otherwise, a victim can unknowingly download malware after visiting a malicious website or downloading a fake app.
TALK TO A FRAUD FIGHTER
The impact of remote access attacks.
-
800Mdollars was the cost to victims to remote access scams in 2022 alone.
-
230%more remote access scams in 2022.
-
18,000victims reported total losses of nearly $588 million in 2022.
Detect remote access tool use before the scammer can steal the money.
Remote access attacks pose a significant threat to financial institutions and their customers. Attacks involve fraudsters deceiving customers into downloading Remote Access Tools (RATs), granting them control over personal devices. Typical approaches to fraud prevention can’t detect RATs, allowing fraudsters to bypass any security measures. Using advanced analytics powered by artificial intelligence and machine learning, ThreatMark can identify signals of device manipulation by a fraudster when remote access tools are installed. Additional signals of remote access attacks include the nature of mouse movements when the fraudster has taken control of the session and the overall length of the session.
The impact of remote access fraud is twofold: customers suffer financial losses and compromised personal data, and the institutions meant to protect vulnerable individuals face reputational damage and the burden of rectifying such breaches.

Preventing remote access attacks.
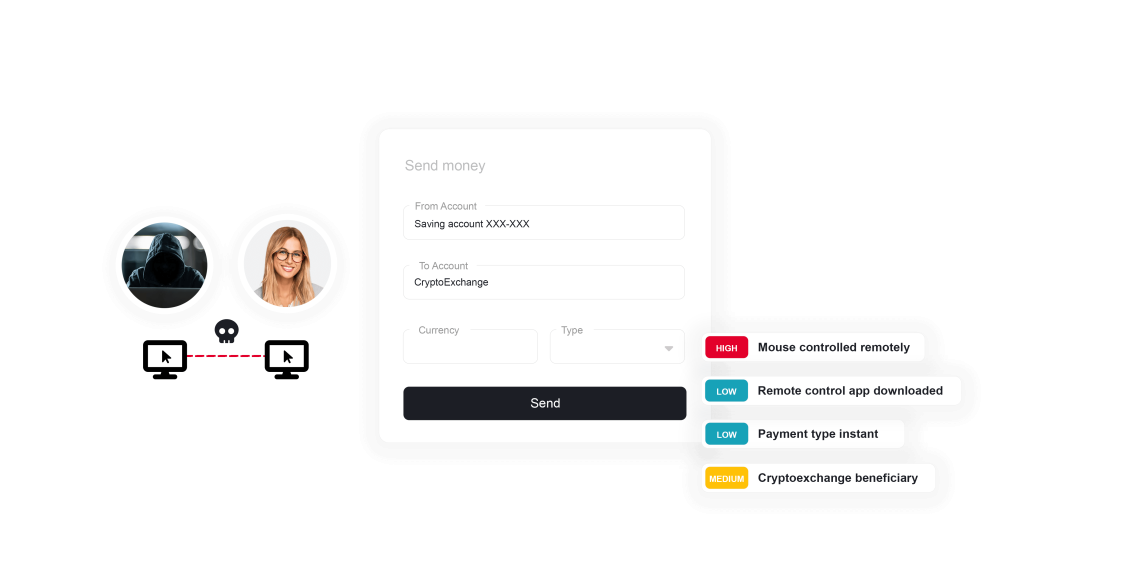
Understanding ThreatMark’s approach to remote access attacks.
-
Remote Access Attacks
Legacy fraud prevention measures have limited effectiveness in detecting remote access attacks. When a session is controlled remotely by fraudsters, a bank's systems may identify the device as trusted based on its fingerprint or other biometric authenticator, which may not show any signs of malware and may appear to have the correct IP and geo-location.
-
Remote Access Tool in Use
When scammers have convinced an unsuspecting customer to install a remote access tool, this opens the door for the scammer to hijack the user’s legitimate session. The moment the scammer starts using the tool, things like how the mouse is moving and how the keystrokes are received, among other indicators, reveal that a remote access tool is in use.
-
Remote Access Tool Available
Remote access tools allow for remote manipulation of a device, but they also expose hardware indicators that reveal their presence. These indicators can be used to increase the risk suspicion of the banking session, and when seen in combination with other risk factors, they lead to the detection of a remote access attack.
Want to learn more about ThreatMark?
Complete our form to discover more about ThreatMark’s comprehensive approach to fraud disruption.