Scams & Social Engineering
Modern scam techniques have evolved.
Scams now target customers, not just their accounts. Fraudsters commonly avoid direct interaction with banking platforms, preferring to manipulate victims into conducting the transaction. Traditional fraud detection methods are therefore ineffective as the legitimate user is logging in to their accounts from their own devices and locations, with appropriate credentials to carry out the transaction.
Winning the war against scams and social engineering.
TALK TO A FRAUD FIGHTER
Scams and social engineering fraud represent a very real threat to individuals and their life savings. By impersonating a trustworthy person or feigning romantic interest, scammers exploit the victim’s misplaced trust and manipulate money movement services such as authorized push payment (APP). These techniques, such as coercion via phone calls, emails, messages, websites, or social profiles, are used to extort money or steal credentials. Traditional monitoring systems, however, only look at the transaction, making these developing techniques challenging to prevent.
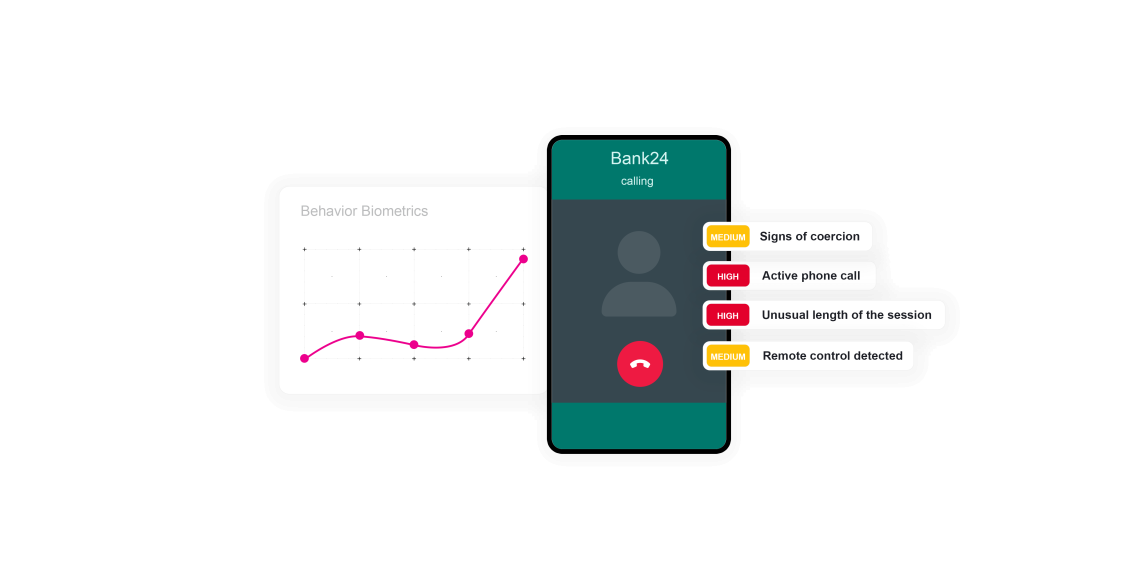
Winning the war against scams and social engineering requires arming organizations with the right tools at the right time. ThreatMark examines customer behaviors to detect signals that a user may be under coercion when attempting to conduct a transaction.
ThreatMark’s behavioral intelligence solution understands the subtle differences in user behavior to continuously validate the user’s identity, protecting their most valuable assets and successfully preventing social engineering scams.
The hard truths.
-
32%of financial institutions have seen an increase of losses of 10% or more.
-
48%of financial institutions executives see Scams and Social Engineering as the greatest threat.
-
110.8%increase in reported scams between 2019 and 2021 (and only 7% of scams are reported).

Stop scams before they occur.
Types of scams and social engineering fraud.
-
Instant Payment Scams
Instant payment scams exploit the speed of electronic transactions, tricking victims into making immediate payments under false pretenses. Common tactics include fake invoices, lottery winnings, or urgent requests for help. Once the payment is made, it's often irreversible, causing financial losses and highlighting the need for caution in online transactions.
Learn More
-
Authorized Push Payment Scams (APP)
Authorized Push Payment (APP) scams are a sophisticated fraud involving perpetrators tricking individuals into willingly transferring funds to an account controlled by money mules. Perpetrators disguise themselves through convincing stories, exploiting trust to manipulate victims into authorizing payments.
Learn More
-
Investment Scams
Investment scams lure individuals with false promises of high returns or exclusive opportunities. Perpetrators may use fake investment platforms, Ponzi schemes, or pressure tactics to persuade victims to invest. Once funds are transferred, scammers disappear, leaving victims with significant financial losses.
Learn More
-
Peer to Peer Fraud
Peer-to-peer (P2P) fraud involves deceptive practices within direct transactions between individuals. Scammers exploit platforms facilitating peer-to-peer interactions, such as online marketplaces or payment apps. They may use fake profiles, misrepresent items, or employ various schemes to defraud unsuspecting users, often resulting in financial losses.
Learn More
-
Romance Scams
Romance scams involve fraudsters building fake romantic relationships online. The fraudster creates a fictitious personas to emotionally connect with target, gaining trust over time. They then exploit this trust to request money, often citing emergencies or personal crises. Victims, emotionally invested, suffer significant financial losses and emotional turmoil before realizing.
Learn More
-
Purchase Scams
Purchase scams deceive buyers through fake online listings, often on e-commerce platforms. Scammers offer goods or services at attractive prices, enticing victims to make payments but the purchased items never arrive or are vastly different from descriptions. This emphasizes the importance of verifying sellers and using secure payment methods when making purchases.
Learn More
FAQ: Scams and Social Engineering
-
How can financial institutions protect their customers from scams?
Scams and social engineering fraud are evolving. Fraudsters are taking advantage of human vulnerabilities, and it’s clear that for financial institutions to protect their customers, active detection across all digital channels must include device behavior monitoring.
ThreatMark employs AI-powered methods to monitor banking systems in real-time. The continuous monitoring and authentication enables detection of deviations that may indicate fraudulent activity, allowing for financial institutions to take immediate action to prevent potential fraud.
-
What are indicates of a scam in progress?
Examples of signals that could indicate an active scam in progress could active phone calls during the banking sessions, the overall duration of the banking session, and whether the beneficiary account is new to the customer.
-
What’s New in 2024: ThreatMark Among Top Startups and a Website
As 2024 progresses, so do we at ThreatMark! For the third consecutive year, CzechCrunch has included us in its CC25 list of the top 25 most intriguing startups.
Read More
-
On Widespread Holiday Delivery Scams & How To Prevent Them
As Christmas is quickly approaching, everyone is trying to get ahead of buying presents. Given the pandemic we’ve been living through in for the past two years, consumer habits have shifted to online shopping.
Read More
Want to learn more about ThreatMark?
Complete our form to discover more about ThreatMark’s comprehensive approach to fraud disruption.