
Peer-to-Peer Fraud
In a Peer-to-Peer (P2P) scam, fraudsters impersonate legitimate businesses or people with a seemingly legitimate reason to request money.
duping victims into paying for goods or services never delivered. Often, these scams involve the victim voluntarily sending money through fast transfer services like Zelle or PayPal, usually during a phone call. The fraud hinges on the fraudster convincingly presenting themselves as linked to a credible organization, leading the victim to execute a payment under false pretenses. Additionally, P2P scams can occur through unauthorized access to a victim’s account, resulting in payments made without the victim’s consent.
TALK TO A FRAUD FIGHTER
The impact of peer-to-peer scams.
-
1.7Bdollars of P2P fraud losses in 2022.
-
8%of all banking customers say they’ve been victimized by a P2P scam in the last 12 months.
-
42%of adult Americans have used P2P apps in the past week.
Bolster protection of peer-to-peer transactions.
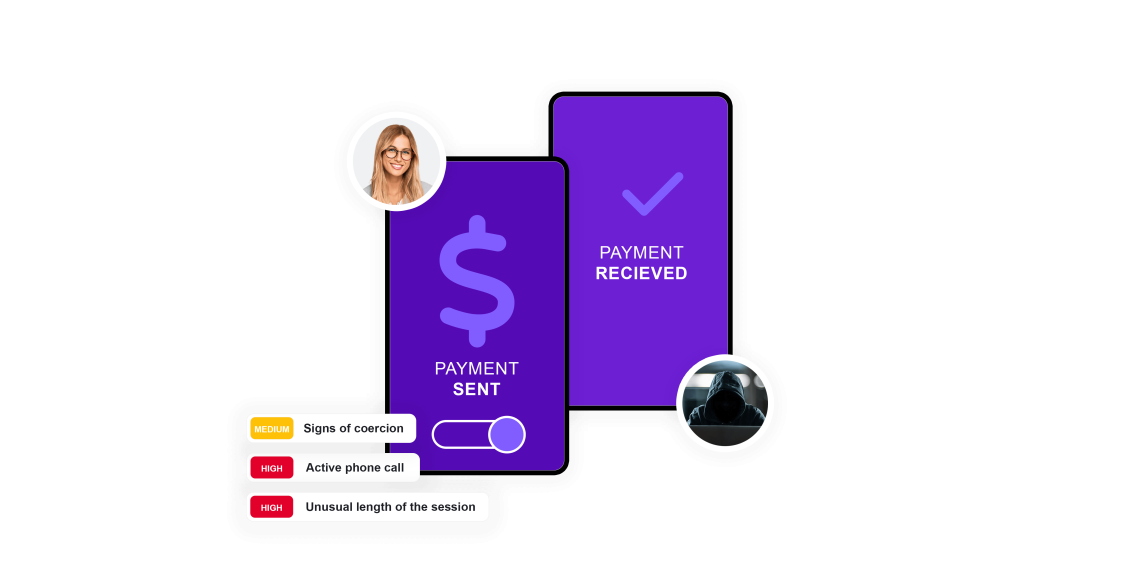
ThreatMark offers a vital tool for financial institutions to thwart Peer-to-Peer (P2P) scams. By analyzing customers’ transaction histories, ThreatMark can detect unusual activity, such as sudden, large transfers to unfamiliar accounts, which could signal a scam. The system also identifies patterns deviating from a customer’s normal behavior, like an atypical frequency of transactions or unusual payment methods. This proactive monitoring allows for real-time detection of potential scams, enabling the financial institution to intervene promptly, possibly freezing suspicious transactions for further verification.
ThreatMark can identify instances where a customer’s account may have been compromised, leading to unauthorized payments. It does this by tracking login patterns and transaction locations and flagging any anomalies that could suggest unauthorized account access. Through continuous learning and adapting to new scam tactics, behavioral intelligence provides financial institutions with a dynamic defense mechanism against P2P scams, enhancing the security of customer transactions in an increasingly digital financial landscape.

Disrupting peer-to-peer fraud.
Understanding peer-to-peer fraud.
-
Instant Payment Scoring
During vishing attacks, fraudsters employ evasive strategies to avoid detection, ensuring they can finish the transaction before being blocked. One of these strategies is to use high-priority transactions like instant or express payments. One way to block these fraudulent transactions is to scrutinize the priority attribute of a payment.
-
Abnormal Payment
The payment amount, time of day or day of the month of transfer, and the beneficiary can all be analyzed for risk to uncover if the payment is abnormal. Looking at the context of the payment in combination with other risk indicators can prevent fraudulent payments.
-
Payment Tampering
Payment tampering fraud occurs when an attacker interferes with the payment process to redirect funds, change payment details, or manipulate transaction data, aiming to benefit themselves or a third party. By analyzing discrepancies between payment details typed in the interface and data registered in the backend, ThreatMark can detect modifications in payment data.
Want to learn more about ThreatMark?
Complete our form to discover more about ThreatMark’s comprehensive approach to fraud disruption.