On widespread Holiday Delivery Scams & how to prevent them
As Christmas is quickly approaching, everyone is trying to get ahead of buying presents. Given the pandemic we’ve been living through in for the past two years, consumer habits have shifted to online shopping.
Everyone is now used to packages being delivered straight to their doorstep. With this increased comfort comes an increase in email and SMS notifications about upcoming deliveries.
The fraudsters noticed this trend and mimic the messages from delivery companies to scam unsuspecting victims to gain access to their banking services, steal important credentials and / or steal credit card details.
Some countries have seen a huge increase (700% in the UK) in SMS scam messages in the first half of 2021 compared to the second half of 2020. [1] The parcel and package delivery scams accounted for 67.4% of all scam messages surpassing financial and banking services impersonation, which made up 22.6% of reported attacks. [2]
The SMS based phishing attacks called smishing are especially dangerous because:
- most people aren’t sure what smishing even is. [3]
- 98% of SMS messages are opened and read. [4]
- Links in SMS messages have 8x higher chance of being clicked compared to emails. [5]
The combination of approaching Holidays, and aftermath from Black Friday and Cyber Monday shopping spree means that most people will be legitimately expecting a package and will be less cautious when receiving texts/emails about package delivery which increases the likelihood of scammers being successful.
Our research indicates that multiple delivery companies are being impersonated by scammers and for their nefarious ends. No company is absolutely safe from the impersonation attempts and scammers target both well-known brands such as DHL, UPS, FedEx, etc; and local carriers.

We’ve seen several different variations of this scam using SMS and/or email as a vector of attack:
- A fee needs to be paid before the package delivery (e.g., VAT) … A link in the message takes you to a fake site that will collect your personal and/or credit card information.
- The package is held up at an office/depo and confirmation of delivery time is required… This site will try to collect your personal information and it may be sold or misused in the future.
- The package could not be delivered, and you need to reschedule delivery… Same as the previous example.
- The package could not be delivered, and you need to install an app to track it/reschedule delivery…
- The linked app is usually malware that will either install additional malicious programs, steal your banking information or make transactions.
An example of how a phishing site can be served via SMS is as simple as this one:
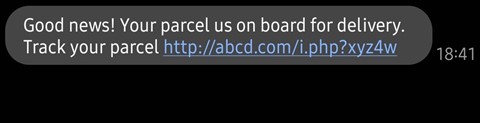
This type of obscure links can contain various threats. From a fake banking portal, an online credit card form that is controlled by a fraudster; to malware.
We have found a malicious application that uses overlays to steal banking credentials and is masquerading as a package delivery application in another article (read about FluBot Banking malware in detail in our blog post here).
It is important to know that sometimes the application that is installed is a “dropper”, which is an application that may have (or pretend to have) some functionality, but its main purpose is to install other malicious applications to your device later.
How do the attackers know your email/phone number?
You may think that these scammers can’t get to you as you keep your phone or email private to yourself. But this is a wrong and dangerous assumption in today’s digital world.
You’d be surprised how much information is publicly available to anyone through social media alone. And beyond social media database of specific and legitimate user information can be found on the internet. This information is usually sourced from breached databases of various sites and e-shops.
It’s always safe to be extra cautious, aware and critical of your digital security. Your email account itself could be compromised and the attacker, as in the example of these threats, might be checking your actual emails, looking for information about real deliveries.
This way the fraudster has the correct delivery company name and a time-frame for the delivery so that the malicious message he sends will have an even greater chance of success.
Luckily, it’s rather easy to verify if your email address or phone number was a part of a known leak via the website: https://haveibeenpwned.com.
Again, being a healthy skeptic, you should note that this website aggregates only known data breaches. There might be some information leakage or specific hacks that never get to be analyzed and investigated by cybersecurity researchers, the good guys.
How to prevent holiday delivery scams?
Preventing similar social engineering scams (with account takeover intentions) can happen on two distinct levels: on the target business and the user’s side. On both levels, 2 major levers prevent such scams: education and technological solutions.
Although the great portion of preventing social engineering scams relies on the end-users; arguably, the companies have more incentives to invest significant effort in fighting these scams.
Companies should invest in continuous education of their users about the threat, details and presentation of social engineering, phishing and similar scams. Conversely, businesses can invest in an advanced technological solution, such as ThreatMark, that can detect and mitigate fraud at scale.
Both methods of prevention are especially relevant for the banks and financial institutions since they manage and (should) safeguard consumers’ most precious assets.
At ThreatMark we take cybersecurity and fraud prevention very seriously. Our advanced fraud prevention solution with comprehensive threat detection is used by banks throughout the world to stop fraud and ensure the client’s assets are safe, sound and out from the scammers’ reach.
Our technological solution is complemented by a Security Operation Center (SOC) team whose core responsibility is to provide banks with advanced threat detection, mitigation and prevention.
Also, we actively work with the banks by providing education, workshops and advice for threat prevention and mitigation. And we produce educational content, such as this, publicly to increase awareness of cyber threats and offer prevention advice more broadly.
End users of course can use technology to help prevent these scams – such are anti-virus and anti-malware software for their devices. But, often the users don’t purchase the most comprehensive solutions nor the latest ones.
At the same time, it is with awareness and education that the end-users can increase their safety and well-being in the digital world. In this particular holiday delivery scams, we offer the following advice.
What to do if you receive a suspicious SMS/Email?
In case you received a suspicious message, please be mindful and:
- Don’t respond to the message.
- Don’t click any links.
- Lookup contact information from the official website and call them to confirm, that you received a message from their company and that it seems suspicious.
- If you discover that indeed the message is a part of a scam, report it to the national cyber security organization as well as to the organization that is being impersonated. This will help prevent future frauds.
- Delete the message.
- Block the number/email address.
What if you already clicked the link?
- Close the browser window.
- Scan your device for malware by using any well-respected anti-virus or anti-malware software.
What if you provided personal or banking information to the phishing site?
If you supplied banking information to a suspected phishing site, immediately:
- Call your bank and report the incident, including whether credit card information was shared or not so that it can be blocked.
- You may request chargeback in case a transaction was already made with your card in the meantime.
What if you installed a malicious app from the link?
If you suspect you installed a malicious app – malware – on your device be mindful that anti-malware solutions may not clean your device completely.
To be sure you’ll remove the malware you can factory reset your device. Creating a backup of your phone before the factory reset is not advised as the device is already compromised. You should also change passwords for all financial apps installed on your phone.
[1] ITPro, Smishing attacks increased 700% in first six months of 2021, https://www.itpro.co.uk/security/scams/360873/smishing-attacks-increase-700-percent-2021 (last accessed 30.11.2021)
[2] Proofpoint, 2021 State of the Phish Report, https://www.proofpoint.com/us/resources/threat-reports/state-of-phish(last accessed 30.11.2021)
[3] Ibid.
[4] Rebrandly, 12 SMS marketing statistics, https://blog.rebrandly.com/12-sms-text-message-marketing-statistics/ (last accessed 30.11.2021)
[5] Tom Wozniak, Forbes, What’s Old Is New Again: SMS Marketing, https://www.forbes.com/sites/forbescommunicationscouncil/2019/09/13/whats-old-is-new-again-sms-marketing/?sh=c04eaf146734 (last accessed 30.11.2021)