On Vishing Attacks and How to Prevent Them
Recently we’ve seen an increase in all types of frauds that attempt to misuse the user information for malicious means.
Previously we wrote about how hackers are using Coronavirus fears to steal money through phishing and malware-based attacks.
Similarly, vishing attacks are on the rise and we’ve reported several vishing vectors in action. These are mainly driven by increase usage of multi-channel banking system and 2 factor authentication methods (2FA).
The goal of this article is to shed some light on the vishing attacks, provide advice on how to mitigate these, and show how ThreatMark helps banks prevent and mitigate these attacks completely.
What is vishing?
Vishing, a compound from voice phishing, is a type of attack where fraudsters try to convince unsuspected users to provide them valuable information over the phone.
The valuable information can of course include any sensitive information (that can be further used for additional social engineering), credit card numbers, credentials and so on.
Vishing follows the familiar social engineering setup: An attacker creates a scenario to prey on human emotions, commonly greed or fear, and convinces the victim to disclose sensitive information, like credit card numbers or passwords. In that sense, vishing techniques mirror the phishing scams that have been around since the 1990s. But vishing calls exploit the fact that we’re more likely to trust a human voice — and may target the elderly and technophobic who are naive and have no experience with these types of scams.[1]
Don’t be distracted by the example profile of the victim. Everyone today can be a target of such an attack.
The vishing attacks differ in scope, targets and patterns. And they’re impactful. According to E. Sayegh at Forbes, vishing attacks loss is slowly approaching $50 billion globally.[2]
According to the FBI and CISA, in mid-July 2020, cybercriminals started a vishing campaign targeting employees working from home for US companies. The attackers collected login credentials for corporate networks, which they then monetized by selling access to corporate resources to other criminal gangs.[3]
These attacks are sophisticated and require thorough research and a phishing setup to work.
The phishing pages were made to look like a targeted company’s internal VPN (Virtual Private Network) login page, and the sites were also capable of capturing two-factor authentication (2FA) or one-time passwords (OTP) if the situation required.
Criminal groups then compiled dossiers on the employees working for the companies they wanted to target, usually by “mass scraping of public profiles on social media platforms, recruiter and marketing tools, publicly available background check services, and open-source research.”[4]
Collected information included: name, home address, personal cell/phone number, the position at the company, and duration at the company, according to the two agencies.
These scams are frequent, and their complexity differs. Under the entire vishing attacks umbrella. Hashedout notes 4 common vishing examples:[5]
- Telemarketing Fraud – where fraudsters intend to scam users for payment or quick gain. For an example, ‘a charity needs your help and that you can make a difference with even just a small donation;’. In this case, the charities don’t exist, and the donated money ends up in the hands of the fraudsters.
- Government Impersonations – we’re fraudsters impersonate the government (usually Tax Authorities, Social Security and so on) to scam the users. Here fraudsters use the emergency of a situation to request payments.
- Tech Support Fraud – fraudsters pretending to be tech support for a company. In this case, the fraudster informs the user that something is wrong with their device and they’d need remote access to fix it. Later, they’d charge the user for the problem that didn’t even exist.
- Bank or Financial Institutions Impersonations – financial vishing scams often involve an actor impersonating a bank, credit card company, or another financial institution to get information about your personal, financial, or account credentials.
The categorization above shows how varied and complex these attacks are and they’re not to be easily overlooked.
What can businesses do to prevent or mitigate vishing attacks?
Vishing attacks are targeted at people. And prevention should be observed from that perspective as well.
Businesses should focus on preventing phishing attacks for their end-users and their employees.
Surely, one of the key pillars in stopping any type of social engineering attack is to educate and foster a healthy level of suspicion.
Raising awareness of these attacks and how people can prevent them is not an easy task. It is easy to argue that the information on it already exists and it’s widely distributed.
Though, improvements can be always made. Education is always a good starting point. It can enable both employees and customers to stay aware of the latest attack vectors and explain how they can mitigate them. So, businesses should be certain the message has been communicated and received.
Understandably, with compulsory training and certification on the job, it is easier to ensure employees are aware of the attack vectors than the end-users. But at least some efforts should be given to educating the end-user. An email in a semester or a checkup phone call to the customers would help keep the customer apprised and safe.
Connectedly, businesses usually buy solutions that protect their infrastructure and employees from all sorts of attacks. From VPNs, OTPs, SSOs (Singel Sign On) to all kinds of solutions, security frameworks, and authentication methods – businesses invest a lot to protect their assets from fraudsters.
At the same time – the end-user doesn’t have that luxury. The only protection from vishing attacks they have is the wits and suspicion that something is off place and do not succumb to the fraud.
Some businesses have the means to protect their end-users from vishing attacks altogether. Like banks that use ThreatMark.
Banking vishing attacks in 2020 and how ThreatMark stops them
Our data shows vishing attacks on the banks are increasing in scope and frequency. These are mainly driven by the pandemic fears and increase usage of multi-channel banking systems.
Most recently Czech Banking association noted a specific series of vishing attacks where fraudsters impersonated banks asking for unsuspecting clients’ login info to their online banking.[6]
Our current threat intelligence suggests there are diverse types of vishing attacks on unsuspecting banking users. The major difference lay in the execution device of the fraud. That is—whether the fraud was completed on the user’s computer or the fraudster’s computer.
Accordingly, we define 2 major types of vishing attacks targeting banks and their users in 2020: plain vishing and sophisticated (RAT) vishing.
Plain Vishing
In plain vishing type, the fraudster calls the victim pretending to be the bank and by implying urgency and authority sways the user to share the credentials and/or any other incoming second form of authentication. In this type, the fraud is completed on the fraudster’s computer.
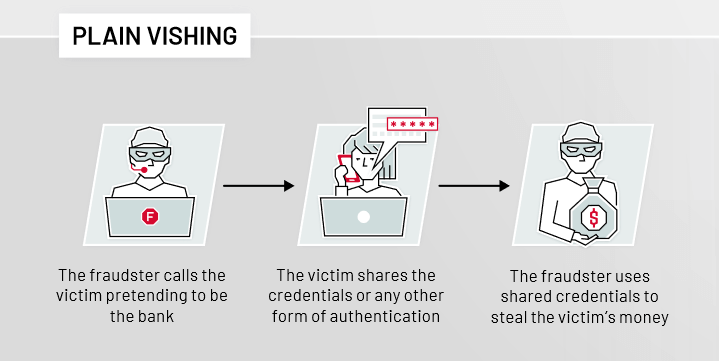
ThreatMark detects these vishing attacks by relying on already built trusted user identity and analysis of various user-specific factors.
Even though the fraudster has taken control of the credentials, has access to the system and other authentication methods—for ThreatMark their attributes are different than the regular user. For example, the device, location, browser, and behavioral biometrics are different than real users. And ThreatMark can identify these differences as irregular and alarming. Accordingly, ThreatMark can elevate the risk factors and sound the ‘alarm’ for that user and/or transaction.
Sophisticated (RAT) Vishing
The sophisticated (RAT – Remote Access Trojan) vishing is a bit more complex as it includes a remote access trojan (RAT) tool. In other reports and resources this category of attacks can be sometimes referred to as: the remote support scam, Team Viewer attack, new wave of vishing attack and so on.
In this sophisticated vishing type of an attack the fraudster persuades the user to install a remote access tool (such as TeamViewer), share the credentials, second authentication factors, and any other information if needed. Once the software is installed by the user, the fraudster assumes control of their computer and continues to use the banking systems as they wish.
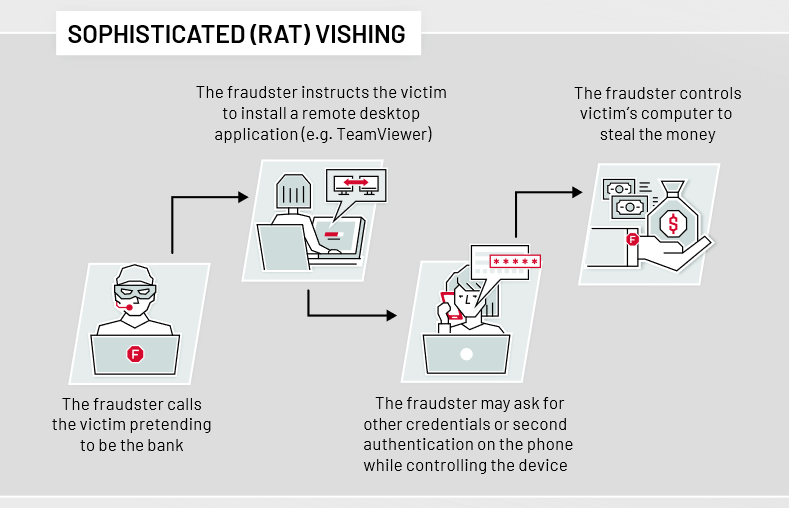
In this case, even though the fraudster is using the user’s computer – ThreatMark can still help and prevent this fraud. Beyond behavior, ThreatMark also detects RAT attacks and diligently raises the risk factor. Additionally, it’s safe to assume that fraudsters will send money to an account that was not used previously by the user. Combined – the anomalies detected in the user behavior and device and the unusual transaction – can be used to raise the risk factors and trigger alerts.
All this information is neatly packaged and presented in our infographic. Which you can also download from here. Use it to help your own organization and users.
Conclusion
Vishing attacks are a type of social engineering fraud where a fraudster convinces the user to provide critical information over the phone.
These types of attacks are ever prevalent and have been causing serious damage around the world. They’re particularly dangerous as they successfully bypass the usual second authentication methods (SMS, email codes and so on).
Vishing attack prevention comes from both the user and the company side.
Users should be ever mindful of such attacks and always foster a great deal of suspicion when being asked for critical information over the phone.
Businesses should do their best to educate their users and get solutions that will prevent these types of takes. Solutions that don’t rely on simple multi-factor authentication, SMS, physical keys, or email alike.
Businesses should invest in solutions – like ThreatMark – that rely on behavioral biometrics and user data to continuously validate legitimate users while keeping the fraudsters away.
[1] CSO Online, Vishing explained: How voice phishing attacks scam victims, Josh Fruhlinger, https://www.csoonline.com/article/3543771/vishing-explained-how-voice-phishing-attacks-scam-victims.html [last accessed: 03.12.2020]
[2] Forbes, Vishing At The Ritz: There’s A New Type Of Cybercrime In Town, Emil Sayegh, https://www.forbes.com/sites/emilsayegh/2020/09/30/vishing-at-the-ritz-theres-a-new-type-of-cybercrime-in-town/#256ac1fa700d [last accessed: 03.12.2020]
[3] ZD Net, FBI and CISA warn of major wave of vishing attacks targeting teleworkers, Catalin Cimpanu, https://www.zdnet.com/article/fbi-and-cisa-warn-of-major-wave-of-vishing-attacks-targeting-teleworkers/ [last accessed: 03.12.2020]
[4] Ibid.
[5] Hashedout – The SSL Store, What is vishing?, Casey Crane, https://www.thesslstore.com/blog/what-is-vishing-how-to-recognize-voice-phishing-phone-calls/ [last accessed: 03.12.2020]
[6] Czech Banking Association, České banky varují před podvodnými telefonáty a e-maily, které ohrožují klienty, CBA, https://cbaonline.cz/ceske-banky-varuji-pred-podvodnymi-telefonaty-a-e-maily-ktere-ohrozuji-klienty [last accessed: 03.12.2020]