Phishing Attacks & How to Prevent Them
Phishing is one of the most prevalent social engineering scams in the internet era.
This article attempts to present contemporary impact of phishing, it’s variations, some interesting trends ThreatMark discovered in 2020; and finally present a direction on how to prevent phishing scams.
Accordingly, we’ll present this complex topic through following sections:
- Short Phishing Definition
- Contemporary Phishing Stats & Impact
- ThreatMark Findings & Phishing trends in banking discovered in 2020
- How to Prevent Phishing Scams
On Phishing
Phishing is a cyber-crime in which a target or targets are contacted by email, telephone, or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords. The information is then used to access important accounts and can result in identity theft and financial loss. [1]
The first phishing lawsuit was filed in 2004 against a Californian teenager who created the imitation of the website “America Online”. With this fake website, he was able to gain sensitive information from users and access the credit card details to withdraw money from their accounts. Other than email-based phishing (including highly targeted spear-phishing), there’s also ‘vishing‘ (voice phishing), ‘smishing‘ (SMS Phishing) and several other phishing techniques cyber-criminals are constantly coming up with.[2]
Based on our data we’ve seen a multi-fold increase of phishing attacks on banks in Europe. These have significantly increased during the COVID19 pandemic. We’ve discovered several different attacks where fraudsters used corona fears to steal credentials and money.
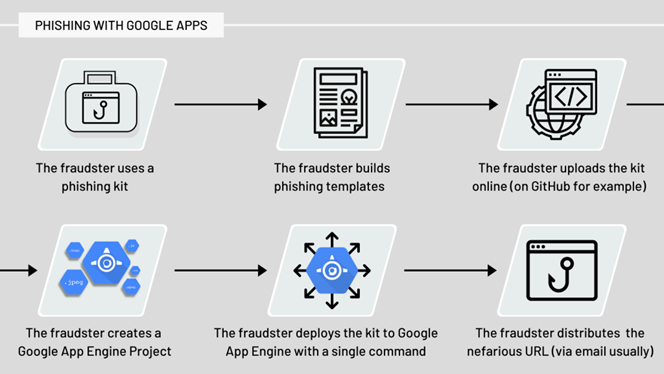
Recently we discovered a new wave of phishing attacks exploiting Google Apps Engine to scale the operations of the attacks.
In essence, all phishing attacks are similar in concept and method. They include using a phishing kit, online deployment and subsequent distribution to the victims.
Example of phishing with Google Apps Engine represented below:
Contemporary Phishing Stats & Impact
Phishing is huge and ever-present in the digital world.
There’s a whole swath of research and investigations that primarily deal with phishing and its impact on businesses and individuals.
According to Verizon’s 2020 Data Breach Investigations Report (DBIR), 22% of breaches (out of 3 905 in total) involved phishing. While this is down 6.6% from the previous year, it’s still the “threat action variety” most likely to cause a breach.[3]
Phishing has been and still is a fruitful method for attackers who use email, 96% of the time, as the main channel for phishing.[4] Per DBIR, the good news is that the open rate is as low as ever, only 3.4%. [5]
These are the top data varieties compromised in the phishing breaches:
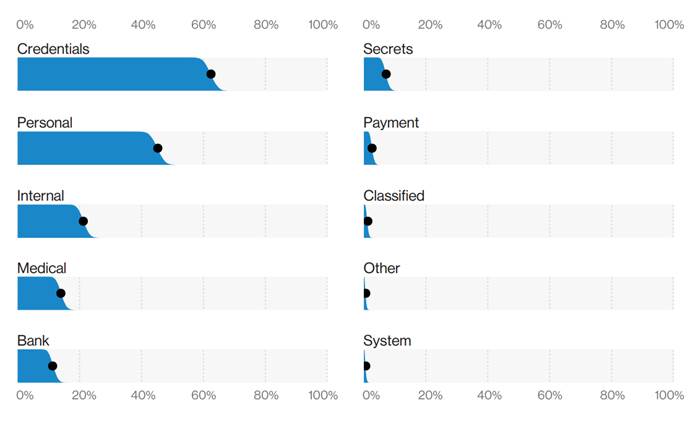
The data from Verizon’s DBIR is also consistent with FireEye’s report on the email attacks which notes that 86% of email attacks are malwareless. Those are impersonation attacks, spear-phishing and CEO fraud email attacks without any malware attached to them.[7]
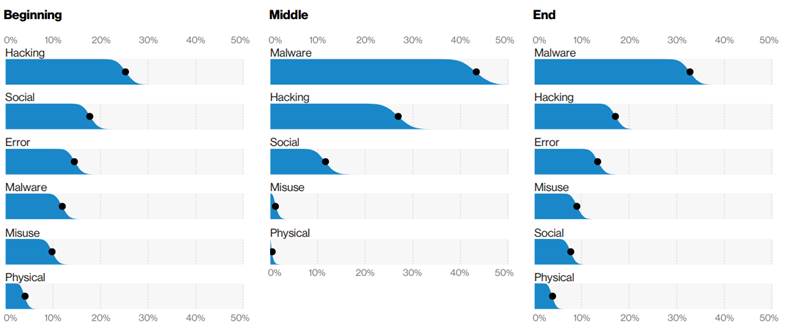
When it comes to a bigger picture, social-based scams, phishing namely, are evident at the beginning and middle phases of breaches and incidents.
While malware glues all that together in the latter stages:
In their research Wandera notes that a new phishing site is launched every 20 seconds.[9] Wandera also notes that the phishing attacks are getting more sophisticated, reaching users in more places, and they are more personalized.[10]
In the mobile-first world, business email compromise (BEC) attacks are moving to other forms of communication such as social media messengers, while spear phishing is made easier on mobile simply by knowing someone’s phone number.[11]
Proofpoint notes that nearly 90% of organizations experienced targeted phishing attacks in 2019 while 88% of organizations worldwide faced spear-phishing attacks and 86% dealt with BEC attacks.
Such prevalence and scalability are impactful.
FBI’s Internet Crime Complaint Center (IC3) received an average of nearly 1,300 complaints every day in 2019, and recorded more than $3.5 billion in losses to individual and business victims.[12] IC3 reports that the most frequently reported complaints were phishing and similar ploys, non-payment/non-delivery scams, and extortion.[13] And at the same time, the most financially costly complaints involved business email compromise, romance or confidence fraud, and spoofing, or mimicking the account of a person or vendor known to the victim to gather personal or financial information.[14]
And it is in the financial and banking sector where phishing is exploding.
In the US fraudsters employed phishing attacks against banks and governmental relief programs using pandemic as a lure. As of April 2020, more than 1500 websites baiting people to disclose personal information were discovered.[15]
ThreatMark Findings & Phishing trends in 2020 for banks
ThreatMark’s Security Operations Center (SOC) complements our technological solution with human threat detection, analysis and mitigation.
From malware, web injects, man-in-the-middle, to phishing or vishing attacks – the SOC team helps our clients identify and mitigate threats 24/7.
Our clients, retail banks around the world, are under ever-increasing phishing attacks which seem to be increasing by the COVID19 pandemic and highly scalable technologies.
In 2020 our SOC team reviewed 4680 suspicious domains. Out of these, 463 were phishing sites that were successfully mitigated.
Interestingly, we saw an incremental increase in phishing sites until June 2020. After a short pause and a decline during the summer — the numbers of detected suspicious and phishing sites grew by the end of the year.
Additionally, we noticed a few key trends when it comes to phishing attacks in 2020:
- The number of SSL enabled phishing websites has increased. APWG’s Phishing Activity Trends Report notes that 80% of phishing sites have SSL encryption enabled.[16]
- URL Shortening services (like bit.ly) were very popular for a brief time
- Phishing site redirects are still popular. Usually, phishing links in emails, which look less suspicious are just redirects to real phishing sites.
- We noted Punycode being used occasionally.
- We see a lot of phishing kits reuse. This points to the proliferation of phishing and the scalability of attacks. Arguably fraudsters are not too willing, or not knowledgeable, to build new phishing kits.
- In our client’s industry geofencing is common. This allows phishing to be accessible, and detectable, from only specific countries or regions.
- Similarly, our SOC team encountered IP blocking on almost every phishing site. Fraudsters are keen to block known security company IPs, bots and IP ranges.
- Occasionally, phishing sites are shown only once per victim (based on IP); after that, the victims are shown no content or are redirected to a search engine.
- Almost all the time the phishing flow contains an OTP/SMS token capture page which suggests automated payment action/app registration or other automation on the attacker’s end.
- And strangely, we even saw some domains being used for multiple banks in multiple regions, some even weeks after they were compromised.
What is worth noting that beyond technical prowess, fraudsters are demonstrating skillfulness when it comes to social engineering.
As we came to realize, the goals of fraudsters go beyond acquiring credentials, but to acquire as much information as possible in order to persuade the victim do what they want in elaborate ways.
Such objectives of the frauds are seen in all RAT attacks and authorized push payments scams. These scams can get really intricate. We’ve investigated several cases where the fraudster called the victim, early in the morning; with background noises from the bank and perfect accent, to scare the victim in sending the money to the fraudster.
Such attacks are trending these days and getting more elaborate from case to case. In essence, this is how a sophisticated RAT attack is implemented:
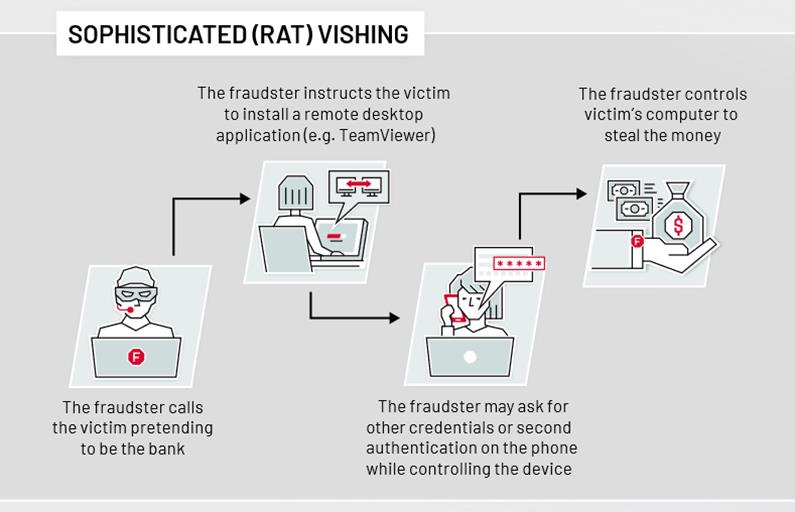
Read more about vishing attacks, here.
On the mitigation side, we’ve dealt with many registrars/hosting providers each with various reporting methods and resolution speeds.
While most of the hosting and service providers are diligent and react fast; we had a few encounters which took a lot of persuasions to remove malicious content from their services. These cases took a lot of effort (communication, escalation) to get resolved.
All findings from our team, and other companies, signify that phishing is here to stay and will remain a very prevalent attack vector. Especially, in the financial services industries.
So, what can businesses do to prevent phishing attacks?
How to Prevent Phishing Scams
Since phishing belongs to a social engineering type of scams, successful prevention of phishing happens on a user and a company level.
On both levels, 2 major levers prevent phishing: education and technological solutions.
Phishing.org notes 10 ways how to avoid phishing attacks and becoming a victim.[17] Seven out of them are educational and awareness related, while 3 are technological solutions to the problem (installing anti-virus, using anti-phishing toolbars and using firewalls).
Proofpoint in their annual State of Phish report, among other results, present two interesting findings.[18] First, the vast majority of organizations said that security awareness training reduces phishing susceptibility. And at the same time: many working adults fail to follow cybersecurity best practices.
And this points to a problem – the significant portion of phishing prevention relies on user education and awareness. And that is tough. Especially considering the prowess and complexity of phishing scams these days.
Intel Security Quiz from 2015 showcases significant challenges users have in distinguishing legitimate emails from phishing emails – wherein 97% of people globally can’t make that distinction.[19]
Although the great portion of preventing social engineering scams relies on the end-users; arguably, the companies have more incentives to invest significant effort in fighting these scams.
Companies should invest in continuous education of their users about the threat, details and presentation of phishing scams. Conversely, businesses can invest in an advanced technological solution that can detect and mitigate phishing at scale.
Both methods of prevention are especially relevant for the banks and financial institutions since they manage and (should) safeguard consumer’s most precious assets.
With ThreatMark banks have an opportunity to use an advanced technological solution as an early warning for active phishing attacks and scams.
How ThreatMark prevents phishing attacks
ThreatMark’s advanced threat detection solution successfully detects active phishing sites. We do this with several innovative methods we have developed ourselves. But also verifying findings with third party data and available APIs.
Combining these methods ThreatMark discovers phishing attacks very early.
Also, complementing ThreatMark’s technological solution is a Security Operation Center team whose core responsibilities is to provide banks total threat detection, mitigation and prevention.
The first task of our SOC team is to validate our technologically-based detection and work with hosting providers and registrars to mitigate all active phishing sites.
Second, the role of the SOC team is to maintain and manage shared Threat Intelligence within the ThreatMark systems. All data ThreatMark collects, from all our clients and users, gets pooled for additional threat pattern recognition and future prevention. This enables our solution to recognize and mitigate phishing attacks before they reach our users and inflict any damage.
And third, our SOC team actively works with banks in providing education, workshops and advice for threat prevention and mitigation.
A real-world example of how ThreatMark’s technological and educational approach in fighting fraud is best witnessed in our work with the banks. Here, you can read how ThreatMark’s helped Sberbank CZ fight online fraud and fine tune its anti-fraud landscape.
Conclusion
Phishing is a social-engineering scam that’s old as the internet itself. Today, phishing scams and attacks are prevalent. Its easy and scalable setup makes phishing a great first step in larger scams that may have various goals.
Ever-increasing, fraudsters are improving their toolkits and using pandemic fears to scam and attack banking institutions and financial services.
Preventing phishing is tough. It includes both educational and technological dimensions that may be implemented from both companies and end-user levels.
Companies can invest in advanced technological solutions – like ThreatMark – that can help the process of detecting, preventing and mitigating phishing attacks before they inflict any damage.
[1]Phishing.org, What is Phishing?, https://www.phishing.org/what-is-phishing [last accessed: 25.02.2021]
[2] Ibid
[3] Verizon, 2020 Data Breach Investigation Report, https://enterprise.verizon.com/resources/reports/2020/2020-data-breach-investigations-report.pdf [last accessed: 25.02.2021]
[4] Ibid.
[5] Ibid.
[6] Ibid.
[7] FireEye, The 3 Ts of an email attack: Tactics, Techniques, Targets, https://content.fireeye.com/one-email/ig-the-3-ts-of-email-attacks [last accessed: 25.02.2021]
[8] Ibid., Verizon
[9] Wandera, Mobile Threat Landscape Report 2020, https://www.wandera.com/mobile-threat-landscape/ [last accessed: 25.02.2021]
[10] Ibid
[11] Ibid.
[12] FBI, 2019 Internet Crime Report, https://www.fbi.gov/news/stories/2019-internet-crime-report-released-021120 [last accessed: 25.02.2021]
[13] Ibid.
[14] Ibid.
[15] Yalman Olaran, Bloomberg, Phishing Attacks Against Banks Jump With Pandemic Used as Lure, https://www.bloomberg.com/news/articles/2020-05-06/phishing-attacks-against-banks-jump-with-pandemic-used-as-lure [last accessed: 25.02.2021]
[16] APWG, Phishing Activity Trends Report¸ https://docs.apwg.org/reports/apwg_trends_report_q3_2020.pdf [last accessed: 25.02.2021]
[17] Phishing.org, 10 Ways To Avoid Phishing Scams, https://www.phishing.org/10-ways-to-avoid-phishing-scams [last accessed: 25.02.2021]
[18] Proofpoint, 2020 ‘State of the Phish’: Security Awareness Training, Email Reporting More Critical as Targeted Attacks Spike, https://www.proofpoint.com/us/security-awareness/post/2020-state-phish-security-awareness-training-email-reporting-more-critical [last accessed: 25.02.2021]
[19] Business Wire, 97% Of People Globally Unable to Correctly Identify Phishing Emails, https://www.businesswire.com/news/home/20150512005245/en/97-Of-People-Globally-Unable-to-Correctly-Identify-Phishing-Emails [last accessed: 25.02.2021]


