New phishing campaigns exploiting Google Apps, targeting banks in Europe
In the last couple of days, we have noticed that a new trend abusing the Google App Engine to host phishing sites has made its way into Europe.
The attacker does not seem to be limited to any specific bank. We have detected and mitigated phishing sites targeting multiple banks in CEE.
Based on our research we suspect a complex, likely automated, and far-reaching operation behind these attacks.
ThreatMark clients are already safe and protected from these threats. We urge other banks in the vicinity to check their systems and probes for the relevant details, as presented later in the article.
On a more general level, this is how phishing with Google Apps works and scales.
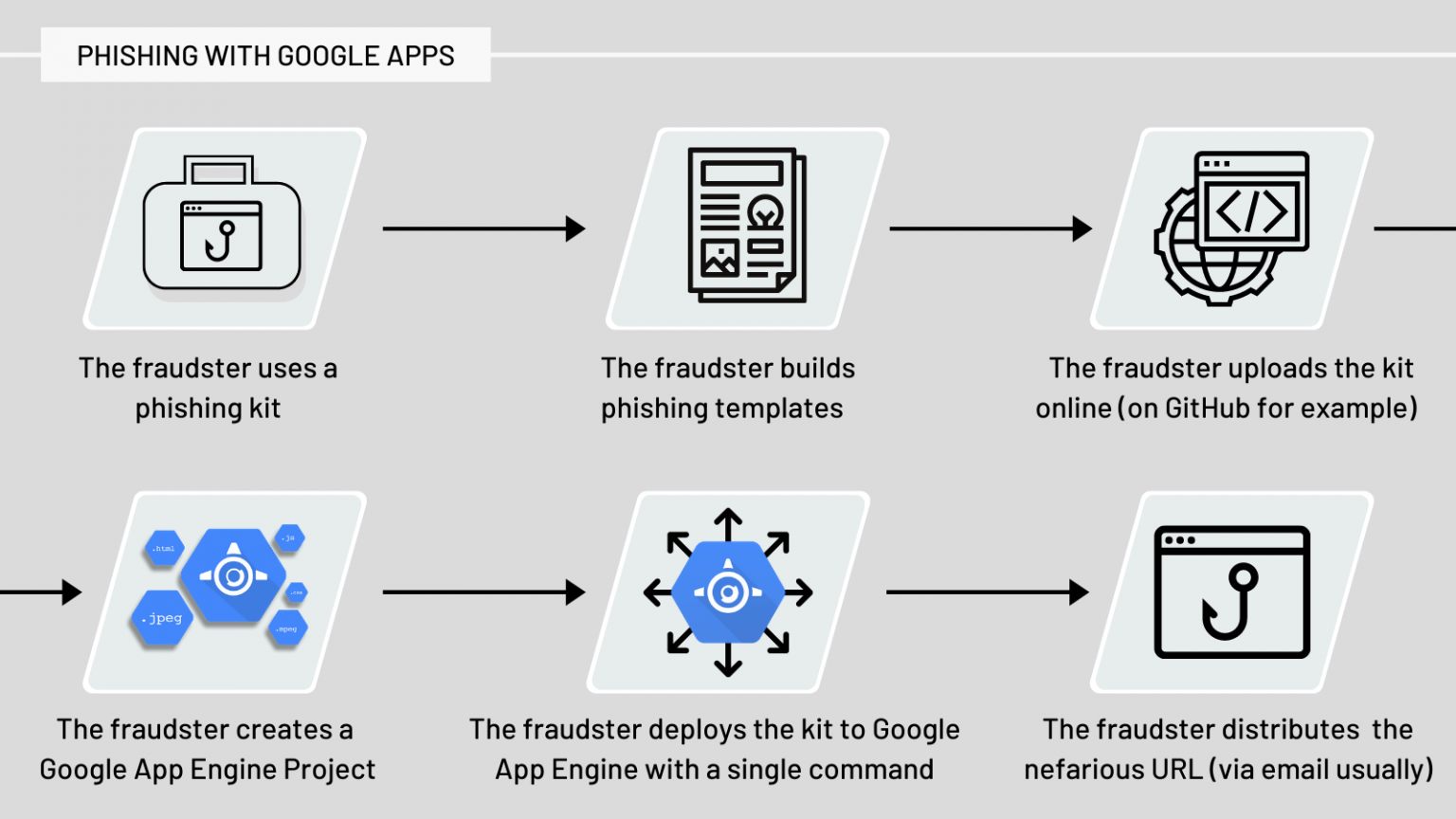
What makes this attack special?
This attack relies heavily on the Google App Engine and its services. Google App Engine is a Platform as a Service for the development and hosting of scalable web applications. The app engine makes the administration of apps easy, which makes this service appealing to attackers. [1]
The Google App Engine service provides an SSL certificate to all apps deployed on it by default. Since the appspot.com domain and all its subdomains belong to Google they are trusted by browsers and security solutions (firewall, antivirus) that might be deployed.
Being hosted on a domain that provides mostly legitimate content means more work for administrators who will have to blacklist individual URLs instead of simply blocking the whole domain.
To further complicate things the Google App Engine URLs may be very dynamic. The URL structure is defined like this [2]:
https://VERSION_ID-dot-SERVICE-dot-PROJECT_ID.REGION_ID.r.appspot.com
However, the URLs we detected use the following format:
VERSION_ID-dot-PROJECT_ID.appspot.com
This means that one app does not occupy a single subdomain but can in theory be found on many unique subdomains for each VERSION_ID, SERVICE, PROJECT_ID, and REGION_ID.
And there’s more. Google App Engine also uses ‘soft routing’.
If a request matches the PROJECT_ID.REGION_ID.r.appspot.com portion of the hostname but includes a service, version, or instance name that does not exist, then the request is routed to the default service. Soft routing does not apply to custom domains; requests to them will return an HTTP 404 status code if the hostname is invalid.
Essentially, this means there can be almost unlimited variations of subdomains that will lead victims to the malicious apps or landing page. The nefarious links only need a valid ‘PROJECT_ID’ and ‘REGION_ID’ field, while others can be random as shown by Marcel Afrahim [3].
And this means that the attackers can be very creative in defining the URLs, making them even harder to recognize and identify as malicious. Especially for non-tech-savvy end users.
Indicator of Compromise & Resolution
Although highly scalable, this attack vector can be easily recognized. Take a look at the sample URLs we discovered:
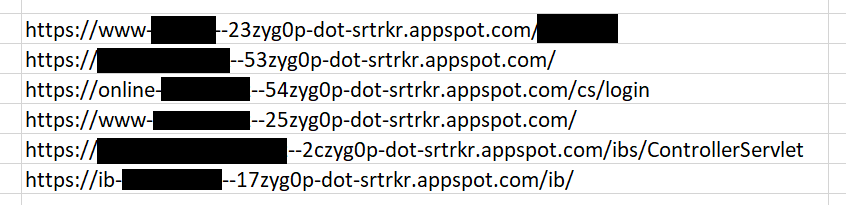
As it is evident, all the URLs share a common substring (PROJECT_ID):
dot-srtrkr.appspot.com
We strongly advise you to refer to your security solutions and logs for this substring and investigate further.
Once you discover the phishing website, head to https://support.google.com/code/contact/cloud_platform_report and submit the URL for a takedown.
In our experience, Google reacted rapidly and diligently to all our requests.
Conclusion
The fraudsters are using the Google App Engine services to build phishing websites on scale and mass. We discovered several phishing sites live for Czechia and Slovakia.
We’re confident this is just a piece of a bigger endeavor. Accordingly, we urge banks to check their security solutions for a common substring: dot-srtrkr.appspot.com.
Taking down these phishing sites can be requested directly from Google at https://support.google.com/code/contact/cloud_platform_report
All ThreatMark clients that have Threat Detection service already enjoy protection and mitigation from these and other attacks.
Our Threat Detection service provides an early warning against phishing threats and swift mitigation and phishing sites takedown. If you’re detecting attacks and experience various security challenges, reach out to us at info@threatmark.com for assistance and mitigation options.
Sources
[1] Google, App Engine, https://cloud.google.com/appengine [last accessed: 22.12.2020]
[2] Google, How Requests are Routed, https://cloud.google.com/appengine/docs/standard/php7/how-requests-are-routed [last accessed: 22.12.2020]
[3] Medium, Attackers are abusing Google’s App Engine to circumvent Enterprise Security Solutions…Again!, Marcel Afrahim, https://medium.com/@marcelx/attackers-are-abusing-googles-app-engine-to-circumvent-enterprise-security-solutions-again-eda8345d531d [last accessed: 22.12.2020]