Transaction Risk Analysis
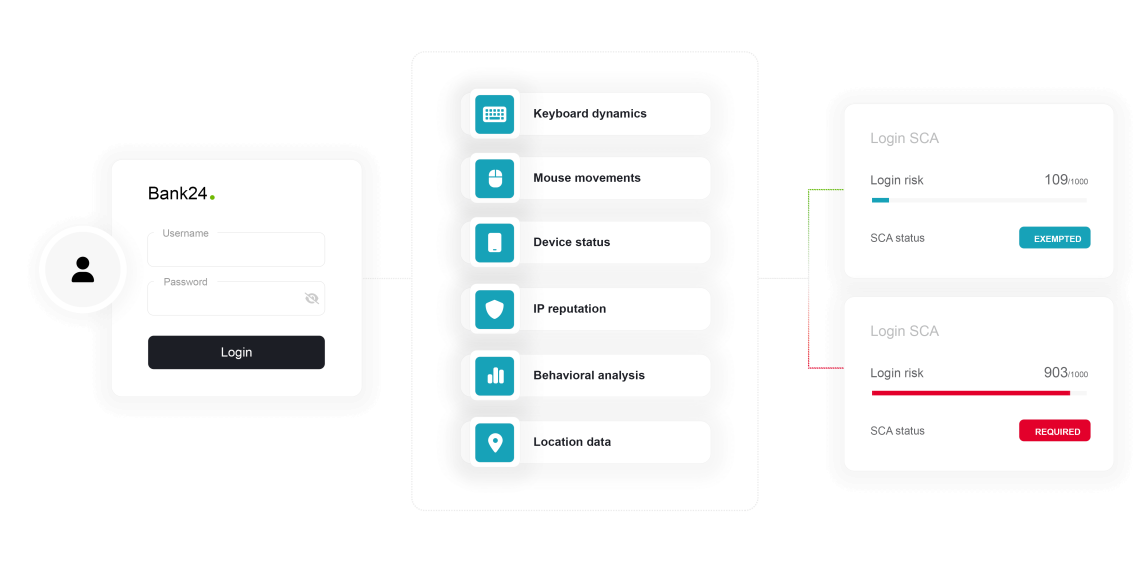
Strong Customer Authentication (SCA) is a security feature mandated by the EU’s Payment Services Directive 2 (PSD2) to help prevent online fraud. The directive requires banks to use multi-factor authentication (MFA) to verify transactions, but MFA can sometimes be inconvenient for customers. To address this, regulators allow banks to bypass MFA for low-risk transactions. To determine a low-level of risk, banks need to analyze various factors of a transaction in real time.
ThreatMark provides a comprehensive solution that considers all necessary factors to avoid unnecessary MFA whenever possible.
Avoid Strong Customer Authentication by using Transaction Risk Analysis.
TALK TO A FRAUD FIGHTER
PSD2, in the European Union, was revised to enhance payment security. It introduces Transaction Risk Analysis, defining how banks need to analyze various factors from banking sessions and adapt security measures upon the analysis. Within this analysis, if a transaction differs from the historical ones or there is a suspicion of compromise, an alert must be triggered, requiring additional authentication measures. Conversely, if no abnormalities are detected, SCA can be waived. Implementing this process and interpreting its results in real time can be challenging.
By design, ThreatMark analyzes the complete list of risk parameters in PSD2 by monitoring and scoring all client activities in real time during the whole session. ThreatMark analyses essential data points, including transaction amounts, locations, device types, payment histories, and user behavior patterns. By providing deep insights into user-specific behavior patterns, ThreatMark allows adapting to consumer behaviors and fraud trends, ensuring accurate risk assessments.
This adaptive approach allows the financial institution to apply stringent security measures for risky transactions while keeping the process efficient and user-friendly for routine, low-risk activities. By integrating ThreatMark’s detailed data, banks can balance security and user experience in their digital channels.

Frequently Asked Questions
-
What are examples of low risk transaction signals?
When ThreatMark identifies a transaction as low risk, it allows the transaction to bypass SCA, streamlining the payment process and enhancing user experience without sacrificing security. Examples of low risk transaction signals include:
- Typical spending amounts
- Known devices
- Matching behavior biometrics
- Regular locations
-
What are examples of high risk transaction signals?
For transactions flagged as high risk, ThreatMark reinforces the need for SCA. By requiring additional authentication methods, the system ensures a robust defense against potential financial fraud. Examples of high risk transaction signals include:
- Atypical amounts
- Unfamiliar devices
- Non-matching behavior biometrics
- Unusual locations
-
Strong & Invisible Authentication
Strong and invisible authentication crucially balances advanced security with a seamless customer experience. Utilizing technologies like behavioral biometrics and behavioral analytics, authenticating users subtly and effectively can minimize the risk of fraud and unauthorized access.
Learn more
-
Payment Transaction Authorization
Traditional transaction monitoring systems often analyze only a limited amount of payment-related data, leading to false positives where even small or insignificant payments trigger an alert because they don't align with the client's previous spending patterns.
Learn more
-
3D Secure Card Payment Authorization
Credit card transactions are a common target for fraudsters as they can easily obtain the cardholder's credit card data without being detected. To prevent this, 3DS introduces two-step authentication to every payment by default.
Learn more
Traditional fraud prevention tools are no longer enough.
Speak with a ThreatMark Fraud Fighter to find out more about our comprehensive approach to fraud disruption.