Strong & Invisible Authentication
One of the authentication challenges for financial institutions is balancing secure authentication without jeopardizing customer experience.
Legacy authentication methods resulted in increased friction without necessarily improving security. ThreatMark operates seamlessly with the authentication system while continuously validating customer identities through deep behavior profiling.
Friction-free, continuous,
and invisible authentication.
Strong and invisible authentication crucially balances advanced security, as required by PSD2’s Strong Customer Authentication, with seamless customer experience.
Entering a one-time password from an SMS/hardware token, answering security questions, or clicking a push notification is cumbersome for the user as these methods can cause frustration and distrust. Traditional authentication methods typically happen only during the login. From that moment onwards, fraudulent activities can often remain completely undetected. That includes cases where a fraudster takes over a session that the victim has already authenticated (after login).
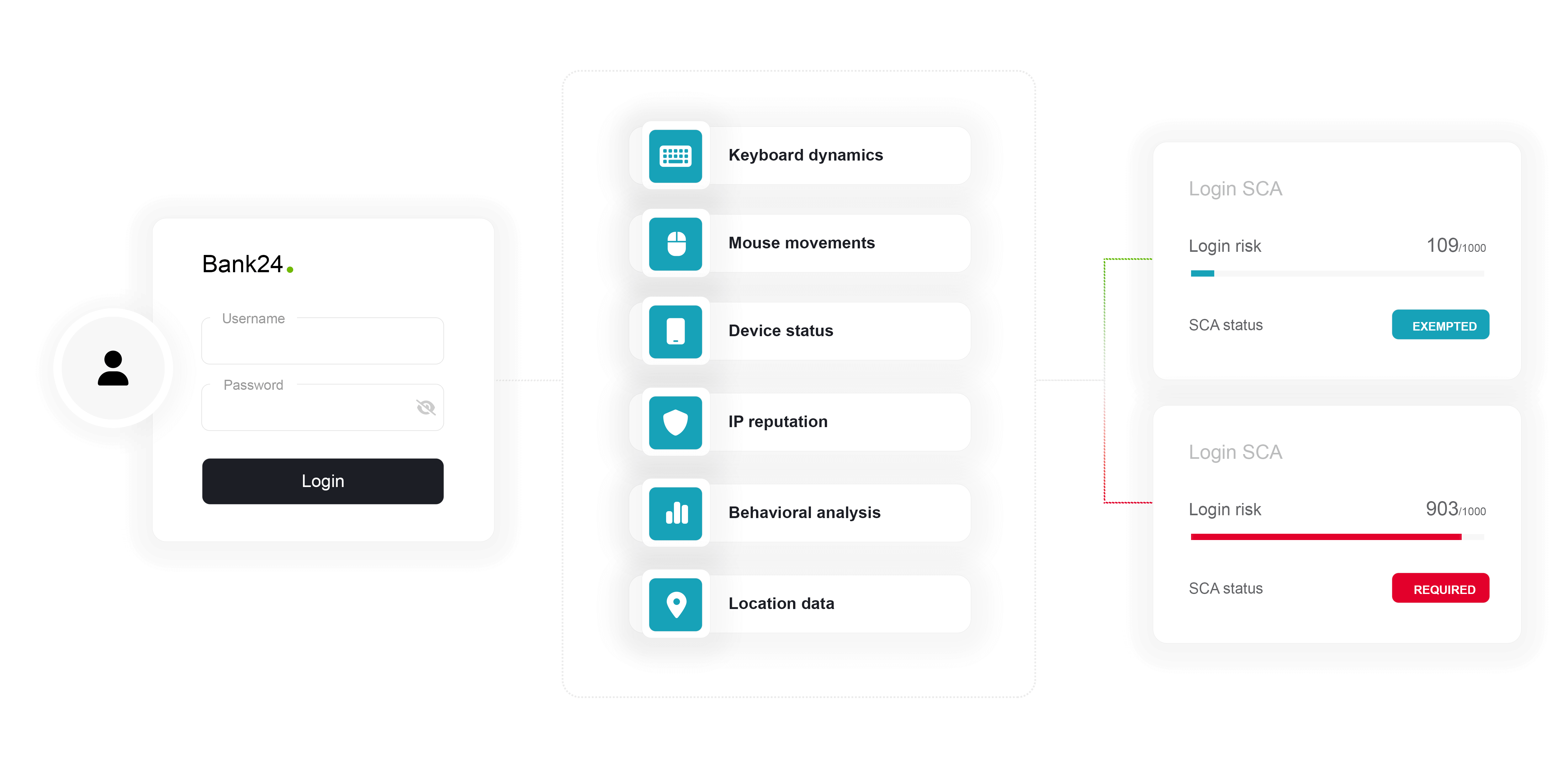
ThreatMark’s approach
to Strong Customer Authentication (SCA).
ThreatMark recognizes the significance of identifying fraudulent activities and implements strong invisible and continuous authentication that powered by deep behavior profiling, consisting of:
- behavior biometrics (patterns in typing, mouse movements, touch events and other interactions),
- typical spending & login routines (unusual amounts, frequency, location, time) and
- security checks (presence of financial malware, outdated browser, rooted phone).
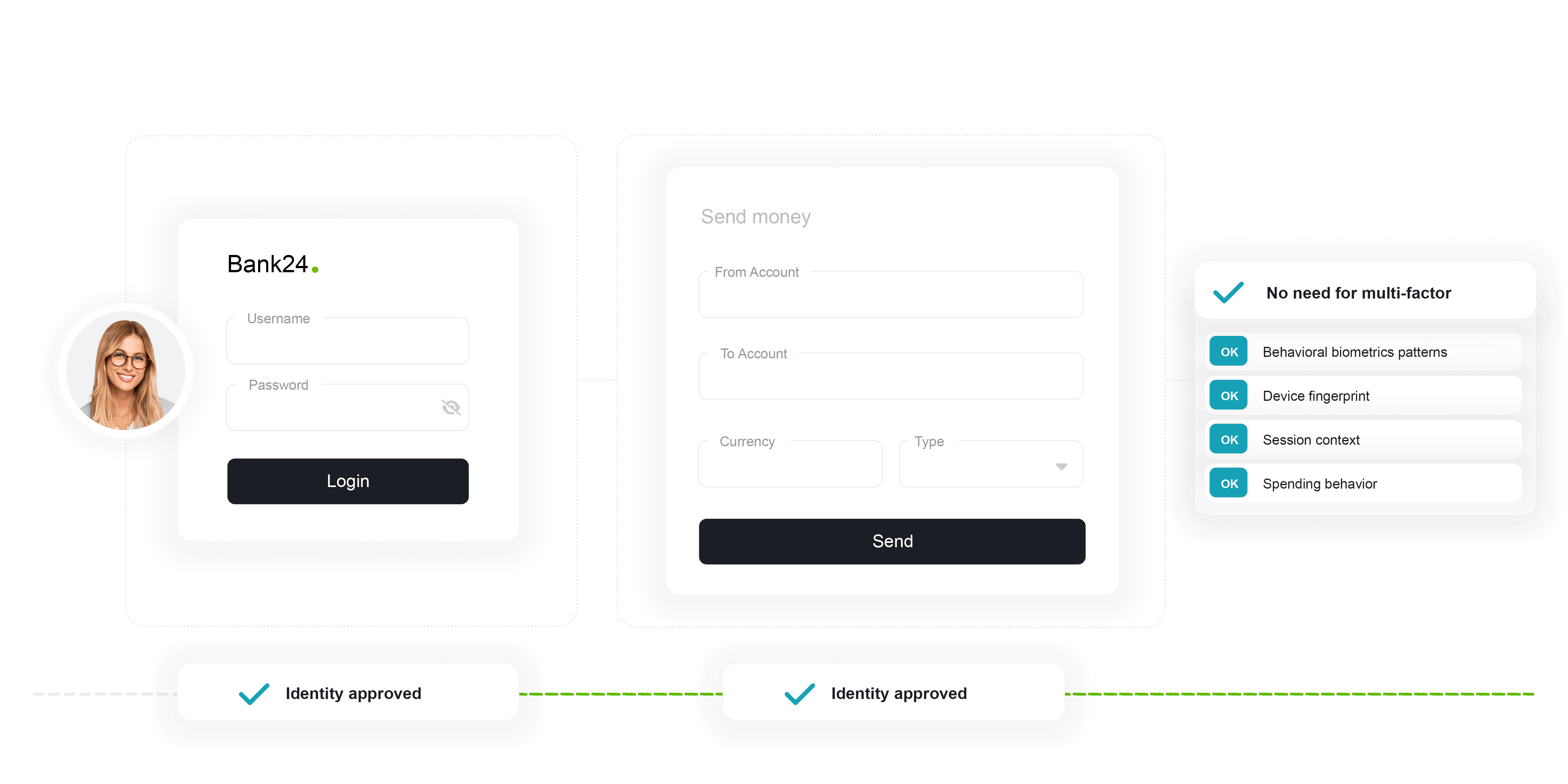
ThreatMark constantly validates every interaction in the background, preventing fraudsters from accessing regardless of the attack vector, including session stealing, RAT, financial malware, or phishing.
Frequently Asked Questions
-
How do phishing attacks abuse SCA?
Multi-step phishing attacks using reverse proxy were used to gain access to accounts. Multi-step phishing frameworks, such as EvilProxy and Evilginx, are difficult to detect. Using phished credentials, fraudsters can instantly log in to the legitimate banking app and generate their own authenticated session, providing them unlimited access.
-
What are other fraud vectors that abuse a lack of SCA?
There are some serious fraud vectors that exploit this single-point-in-time authentication:
- Session stealing where the authenticated token is stolen.
- Remote access attacks involving a session remotely controlled using apps like AnyDesk or similar remote-control software or Remote Access Trojan (RAT).
- Financial malware modified transactions, also known as payment tampering.
-
Why is SCA important to financial institutions?
The ability to continuously authenticate a user makes ThreatMark the ultimate tool for financial institutions seeking to implement reliable, strong, and seamless authentication with proven results (as it has been observed that for more than 90% of logins, ThreatMark suppresses the second factor, which reduced friction and associated costs).
-
Transactional Risk Analysis
To determine a low-level of risk, banks need to analyze various factors of a transaction in real time. ThreatMark provides a comprehensive solution that considers all necessary factors to avoid unnecessary MFA whenever possible.
Learn more
-
Payment Transaction Authorization
Traditional transaction monitoring systems often analyze only a limited amount of payment-related data, leading to false positives where even small or insignificant payments trigger an alert because they don't align with the client's previous spending patterns.
Learn more
-
3D Secure Card Payments Authorization
E-commerce requires strong security measures like 3D Secure to prevent Card-Not-Present (CNP) fraud. 3DS adds an extra layer of security for online credit card transactions but can sometimes cause inconvenience and lead to high transaction abandonment.
Learn more
Traditional fraud prevention tools are no longer enough.
Speak with a ThreatMark Fraud Fighter to find out more about our comprehensive approach to fraud disruption.