How to Detect RAT-Based Fraud in Real Time
Remote Access Trojans don’t make headlines like phishing or APP scams.
In banking, however, they’re one of the most dangerous fraud tools.
Silent and persistent, Remote Access Trojans (RATs) allow fraudsters to hijack a customer’s device, monitor their every move, and ultimately take control of their online banking session.
Worryingly, they are far from rare: RAT families ranked among the most prevalent malware throughout 2024, while law enforcement’s takedown of the Warzone RAT in February and a 196% surge in mobile banking malware highlight just how widespread and urgent this threat has become.
What Is a Remote Access Trojan?
A Remote Access Trojan (RAT) is a type of malware that gives an attacker full, stealthy control over a victim’s device. In banking fraud, RATs are often weaponized as financial malware, enabling attackers to conduct remote access attacks—hijacking online sessions and initiating transactions that appear legitimate.
Unlike simple keyloggers (which record everything a user types) or spyware (which secretly collects information like browsing activity or stored data), RATs act as a backdoor. They allow fraudsters to watch the screen in real time, capture credentials, and even manipulate the device as if they were the legitimate user, including operating banking apps.
What makes RATs particularly dangerous in banking is their invisibility. They often run silently in the background, leaving customers unaware that their phone or computer has been compromised. To the bank, every login and transaction still appears to come from a trusted device, making remote access trojan fraud especially hard to spot with traditional controls.
How RATs Infiltrate Devices
RAT banking malware usually enters a device the same way other malware does, through deception. The most common infection pathways include:
- Phishing emails or messages with malicious attachments or links.
- Fake or trojanized apps, cracked software, or torrent downloads that disguise RATs as legitimate tools or bundle them with popular programs.
- Malicious websites and exploit kits that take advantage of browser or system vulnerabilities—less common today, but still used in targeted campaigns.
For banks, the key point is that even risk-aware customers can be compromised. A single mis-click or download is enough to install a RAT that remains invisible until it is weaponized during an online banking session.
How RAT Attacks Work
Once installed, RAT banking malware creates a hidden communication channel (via specially configured communication protocols set up during the initial infection) back to the attacker. When combined with financial malware techniques, this access can be weaponized in several ways.
- Credential theft — capturing usernames, passwords, or one-time passcodes (OTPs) as the customer types them. These credentials can later be used for a classic account takeover from the attacker’s own device.
- Session hijacking — monitoring or manipulating an active online banking session in real time.
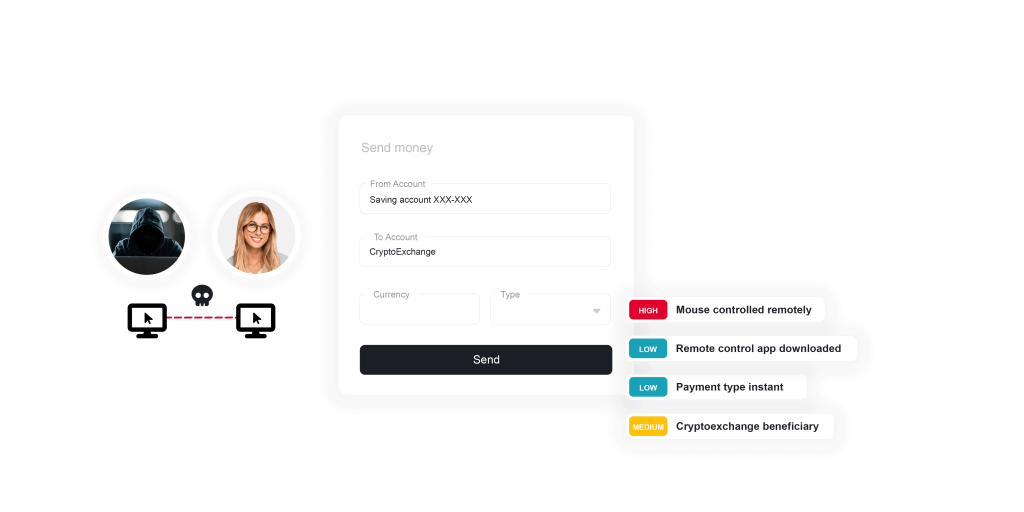
- Transaction manipulation — altering payment details, such as substituting a mule account number during a transfer.
- Device takeover — remotely controlling the customer’s own device during an active session, making every action appear legitimate to the bank’s systems.
The result is a fraud scenario that looks legitimate on the surface but is fully under attacker control, which makes RATs particularly dangerous in financial services.
Real-World Examples of RAT-Related Banking Fraud
RAT attacks continue to surface in live fraud operations worldwide. From mobile apps disguised as legitimate tools to large-scale campaigns targeting entire regions, these incidents demonstrate how remote access capabilities are actively exploited to steal credentials, hijack sessions, and move money out of customer accounts. The following cases highlight the variety of tactics in use and the scale of impact on banks and their customers.
Mobile Remote Access Trojan Fraud in India
In early July 2025, a RAT-based fraud incident in Lucknow saw a victim lose approximately €10,000. The customer received an APK via WhatsApp under the guise of an Aadhaar card update. After installing “iMobile.apk,” attackers gained remote access—reading SMS, intercepting OTPs, operating banking apps—and executed five unauthorized debit transactions on the same day.
Anatsa (TeaBot) RAT Resurfaces in Google Play
In a new campaign, Document Viewer – File Reader, a malicious app disguised on Google Play, infected over 50,000 Android devices. This RAT uses overlay attacks and even hides its activity behind fake “scheduled maintenance” messages to trick users into entering banking credentials. Though recently removed, the event underscores the risk even within official app stores.
Global RAT Campaign via Fake Apps
A broader malware operation targeted Android users worldwide (particularly Australians) using recruiter impersonations to lure victims into installing fake CRM apps. These apps delivered RAT tools like Andidot Banker, which injected fake login forms over legitimate banking apps, effectively stealing credentials and, in many cases, taking over devices.
Zeus, the Original Banking Trojan
Long before today’s mobile-focused malware, the Zeus Trojan (first detected in 2007) pioneered many RAT-style capabilities. Zeus infected millions of devices worldwide and was responsible for hundreds of millions of dollars in banking fraud losses. Its ability to log keystrokes, capture credentials, and manipulate online banking sessions set the blueprint for modern RAT and banking malware operations. After its source code was leaked in 2011, variants like Gameover Zeus continued to wreak havoc for years.
Why RATs Evade Traditional Defenses
RAT banking malware is dangerous because it often slips past endpoint protections. A customer may keep their system updated, run antivirus software, and avoid suspicious links—yet still fall victim. Modern RATs use obfuscation, encrypted communication, and stealth techniques that let them operate silently in the background. As the case examples show, millions of devices worldwide have been infected despite these defenses.
But the real challenge lies at the bank level. Even if infected by a RAT, the customer still logs into online banking from their own trusted device, with valid credentials and multi-factor authentication in place. To the bank’s systems, everything looks legitimate.
This is why RATs are so effective:
- Endpoint defenses miss them — RATs bypass antivirus signatures and remain invisible to customers.
- Bank defenses misinterpret them — Because the RAT acts through a legitimate device and account, traditional fraud detection models often flag nothing unusual.
And this is where banks play a decisive role. As the final line of defense before money leaves the account, banks need RAT fraud protection measures that go beyond device checks and static rules.
Real-Time Detection Signals
Because RATs operate through a customer’s legitimate device and session, the key to RAT fraud detection is spotting the behavioral and technical anomalies that reveal remote control. These are subtle, but when monitored effectively, they allow banks to detect RAT in real time, exposing fraud that would otherwise slip through unnoticed.
Some of the most reliable indicators include:
- Unnatural mouse or touch patterns — Remote operators often move the cursor in straight lines, sudden jumps, or with robotic precision, which is very different from a human user’s fluid motions.
- Copy-paste anomalies — Fraudsters may paste in account numbers, payment details, or OTPs instead of typing them naturally. This deviation from normal customer behavior is a red flag.
- Geolocation mismatches — A customer’s device may show one location, while background connections suggest remote access from elsewhere. This “dual location” can indicate RAT control.
- Rapid screen and navigation changes — Attackers tend to move through the banking app or website much faster than a normal customer would, skipping directly to high-value functions like payments.
- Injected or altered elements — RAT malware can manipulate what’s displayed in the browser or app, introducing hidden fields or modifying transaction details. These discrepancies can signal manipulation.
In addition to these behavioral red flags, RAT banking malware also exposes technical hardware indicators. Remote access tools often leave traces, such as unusual device states or remote-control services running, that can be detected during the banking session. While these alone might not prove fraud, when combined with suspicious behavior, they raise the risk profile significantly and help confirm a RAT attack in progress.
Together, these signals form a behavioral fingerprint of remote control. They don’t rely on whether the RAT malware is known, flagged, or blocked at the device level. They show the difference between a legitimate user and a manipulated session, giving banks the ability to detect RAT in real time and intervene before funds are lost.
Behavioral Intelligence for RAT Fraud Detection
Traditional tools can sometimes pick up the traces of remote access trojan fraud, but what they lack is context. Is the session truly risky, or is it just a false alarm? That’s where behavioral intelligence comes in.
By continuously monitoring both how the user behaves and how the device behaves, banks gain a complete picture of the session. For example:
- Behavioral biometrics reveal when actions don’t match the customer’s unique patterns.
- Technical fingerprints expose when a remote access tool is active on the device.
- Transaction context highlights when payments deviate from the customer’s normal habits.
Individually, these signals might not prove fraud. But when combined in real time, they create a high-confidence indicator of RAT control—allowing the bank to intervene before funds are lost.
This is the strength of behavioral intelligence: not just spotting anomalies, but correlating them into actionable insight that disrupts RAT fraud while keeping genuine customers friction-free.
Discover Our Behavioral Intelligence Platform
Practical Steps to Enhance RAT Fraud Detection
RAT-based fraud highlights a structural gap: even when customers follow best practices, their devices can still be compromised. For banks, this means prevention cannot stop at the perimeter. Response must be embedded directly into fraud operations.
Operationalize In-Session Risk Scoring
Fraud teams should treat RAT indicators not as standalone alerts but as part of dynamic risk models. By correlating remote access signals with behavioral and transactional context, banks can make real-time decisions—whether to step up authentication, hold a payment for review, or stop it outright.
Integrate RAT Intelligence Into Broader Fraud Playbooks
Because RAT activity often overlaps with phishing, APP scams, and mule operations, detections should feed into existing fraud intelligence programs. Linking session anomalies with mule monitoring or phishing alerts, for instance, gives institutions visibility across the fraud chain rather than reacting to isolated events.
Implement Graduated Intervention Strategies
Not every RAT session carries the same risk. Graduated responses, ranging from silent monitoring, to real-time customer messaging, to full session termination, let banks intervene proportionately. This approach balances fraud prevention with customer experience, empowering legitimate users while blocking fraudsters at critical moments.
Leverage RAT Detections to Enrich Threat Intelligence
Every RAT incident reveals more than just an attempted fraud. Remote access tools leave behind technical fingerprints, attacker infrastructure, and mule account traces that can be mapped and analyzed. By treating RAT detections as intelligence sources, banks can expose the wider fraud network, disrupt attacker resources, and prevent similar attempts against other customers. This attacker-centric view transforms detection into proactive disruption.
Closing the Gaps in RAT Fraud Detection
ThreatMark’s Behavioral Intelligence Platform provides banks with the missing layer of defense against RAT-based fraud. By unifying behavioral biometrics, device posture, and transactional context, ThreatMark enables institutions to embed RAT fraud detection seamlessly into their risk models and operational workflows. Instead of treating RATs as isolated anomalies, banks can connect them to broader fraud patterns, enrich intelligence sharing, and disrupt attacks before customer funds are at risk.
Real-World Impact: How BCR Strengthened Its Fraud Defenses
Theory is one thing, but banks across Europe are already applying these approaches in practice. In our new case study, you’ll see how Banca Comercială Română (BCR), one of the region’s largest banks, integrated behavioral intelligence to protect customers from advanced fraud threats while keeping digital banking friction-free.



