On Mobile Banking Malware
Last week our SOC experts exposed FluBot – one of the most dangerous mobile banking malware currently in circulation.
Its impact and growth rate are worrying and its success is raising many concerns throughout the industry.
FluBot is not an anomaly. Its existence is a continuation of previous mobile malware families. Some of which we’ve noted before in our posts on Banking Malware & Attack Vectors for 2020.
Undoubtedly, as more and more people use mobile devices to access services they use, malicious fraudsters aim to exploit that for their own nefarious goals.
And one of the most impactful ways for that is through mobile malware.
The purpose of this article is to provide a general intro to mobile balking malware, with the content divided into the following sections:
- Definition of mobile malware and its dangers;
- Mobile malware cases and statistics;
- Malware’s impact on mobile banking industry;
- Protection with education & technology.
About Mobile Malware
Malware is an abbreviation that stands for malicious software. It defines any type of software that is designed to harm a device and collect sensitive information with malicious intent. It can infect not only a computer or laptop but also smartphones.
A smartphone gets infected once a person downloads an unauthorized application or file. It is often designed to look like an update or a simple app, but hiding a virus.
For example, this is how a FluBot infection process looks like for an example:
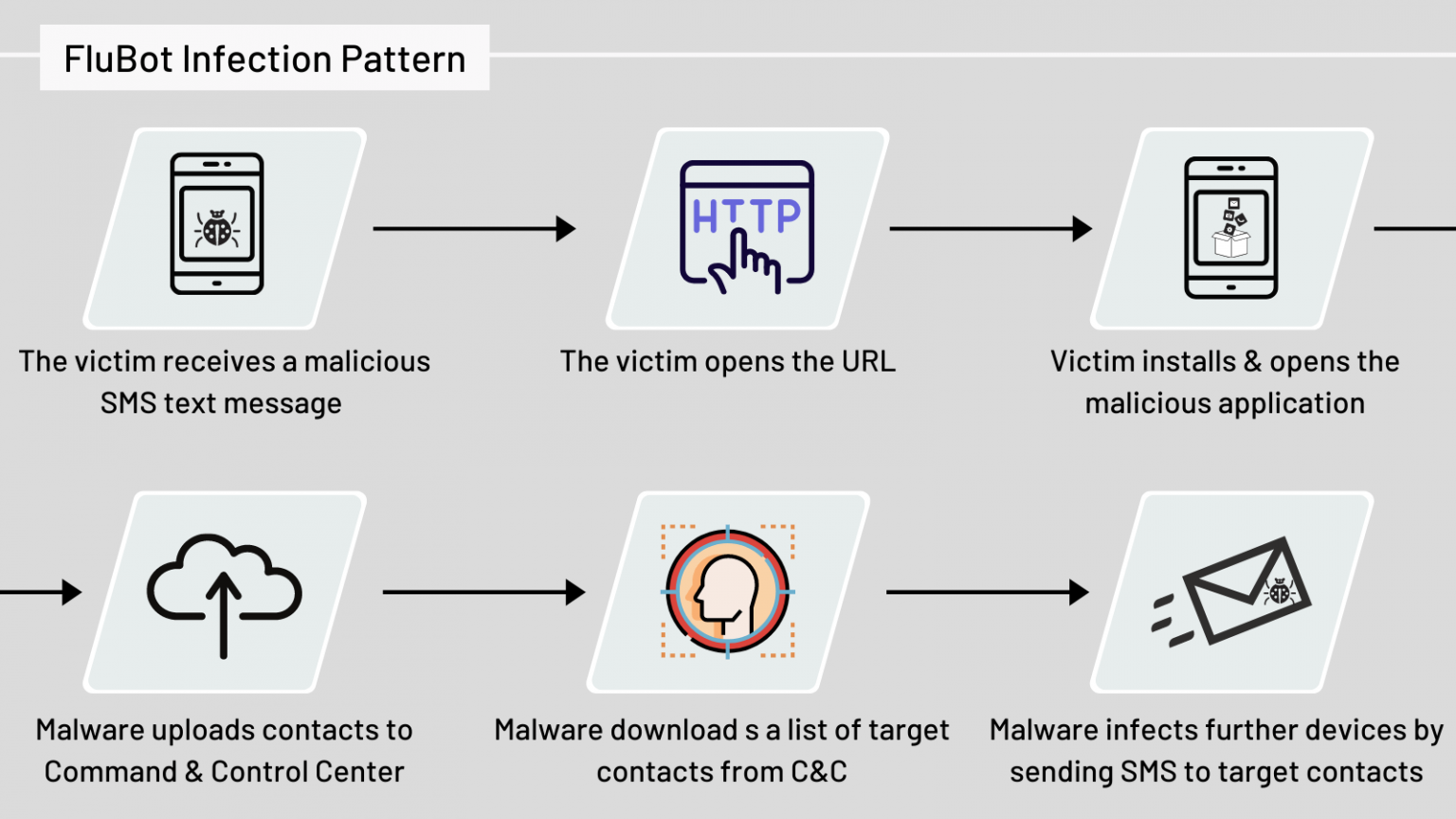
Different malware has different modus operandi and infection processes – some types of malware can monitor all operations on the screen, intercept messages, and even listen to everything by controlling the device’s microphone.
But, in relevance to the topic of this article, there’s one major goal of mobile malware: to get significant rights to manage the device to capture login credentials and other important information (SMS, OTPs and so on).
The Dangers of Mobile Malware
Smartphones are no longer just a communication tool. Nowadays they hold a lot of data—from your favorite dessert recipes to location, work and financial data.
The combined value of all the information on the average smartphone makes malware extremely dangerous.
And no wonder why malware installation is prevalent. In the year 2021, 46% of companies had at least one employee that downloaded and installed a malware mobile app.[1]
And that’s a lot. Especially considering the malware’s ‘nature’ to infect more devices and rapidly expand using the contacts on the phone.
Here are several ways such malware can get on one’s smartphone:
- Popups and fake alerts on sketchy websites that say that one needs to run a security check or download the new version of a program;
- SMS and email phishing. It can be anything from claiming a prize to proving your identity with your SSN, such messages often hide behind close to the actual ones numbers and email addresses;
- File sharing services – malware can be hidden behind illegal music or movies downloads;
- Fake and clickbait links;
- Unauthorized mobile apps on official platforms, like Google Play or Apple Store.
After the file is downloaded, the user installs the app and gives it normal operating system access, read contacts and many other permissions.
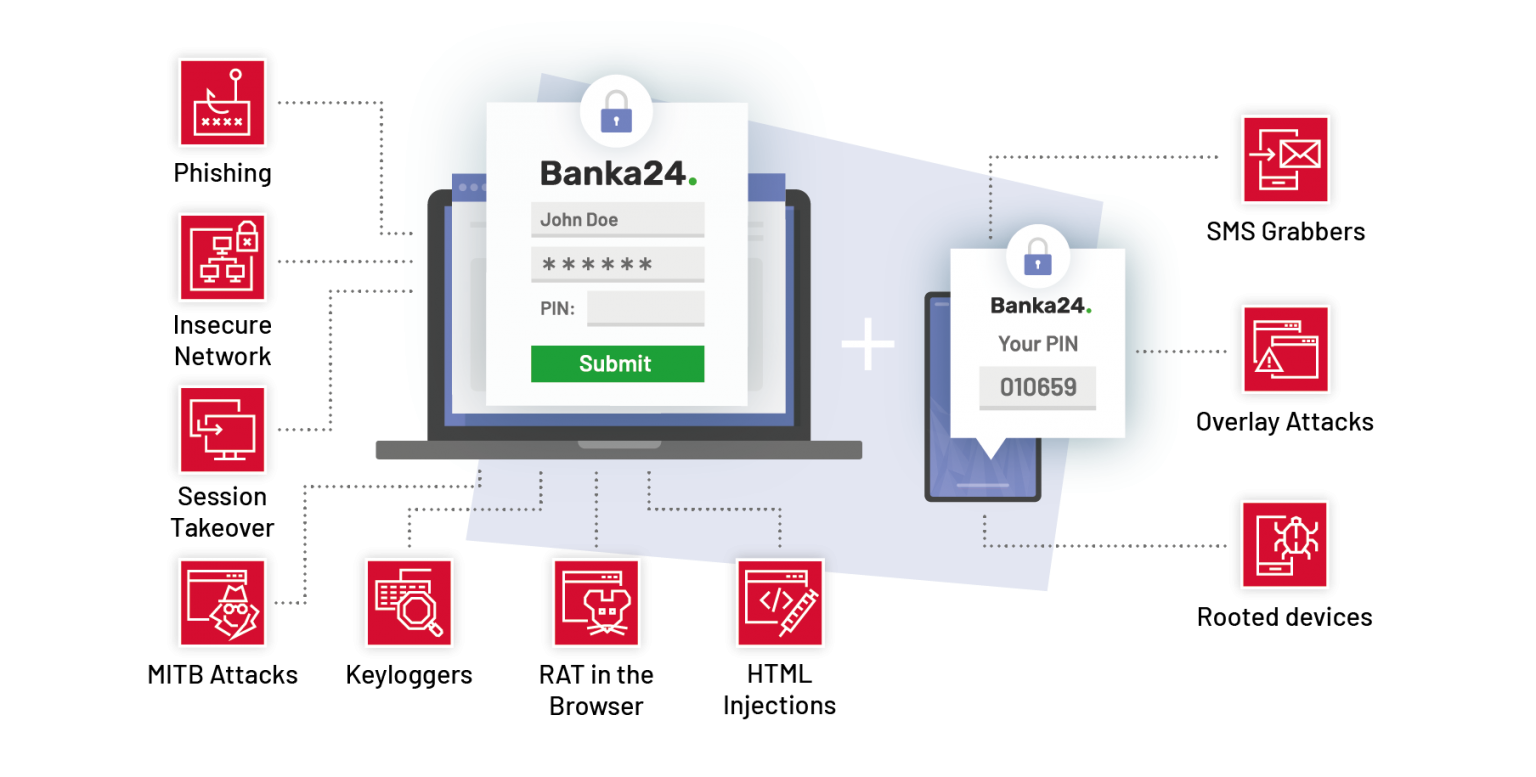
Relevant to mobile banking, malware (like FluBot) can read all windows on display. So when a user opens a mobile banking app, malware can inject the fake login page to gain the user’s credentials.
Just take a look at how FluBot, injects Bankinter overlays into the user’s mobile experience:
Mobile Banking Malware Statistics and Notable Examples
Without getting into numbers and stats, it is hard to see how widespread this problem is.
Just looking into McAfee’s Lab Threats Report will show you the scope and recent exploding nature of this problem.[2]
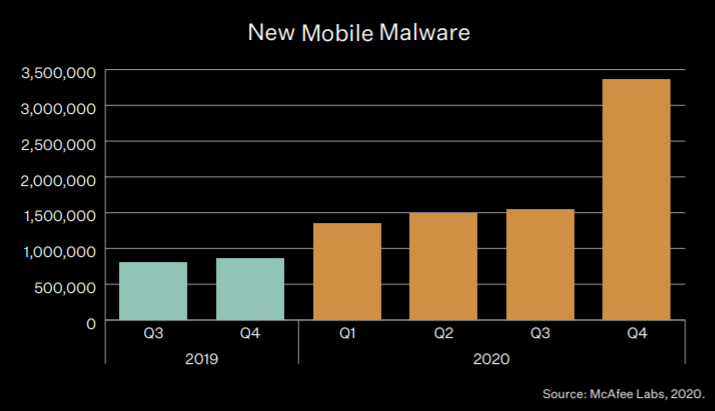
Avast suggests that there may be 100 million devices infected with malware. There are fewer iOS phones, but both sets of users are persistently attacked through the apps they use. [3]
In the malware ecosystem, banking malware is really specific. And beyond FluBot, several other notable malware families wreak havoc.
One of the most known cases of mobile banking malware cases gone wild is Zeus, a Trojan that stole about $47 million from European customers in 2012. Since then it has evolved. The code for Zeus was leaked and it can be traced to many other malware solutions after.[4]
Zeus is designed to crack two-factor authentication. It can intercept text messages from a bank and get access to one’s funds with these security codes. This malware is disguised as a banking software security update. So a lot of people installed it without paying attention much attention to it. When the systems tell you to update the security system, users usually just do it.
As for more recent threats, it is important to mention SlemBunk malware. It has been reported by FireEye.[5] This malware is designed for Android devices and has targeted about 30 different banking applications already. Its main goal is to steal banking login and password. Unlike Zeus, it has a much more complicated chain. A person needs to install three malicious apps on their smartphone before the attack. It makes it incredibly difficult to find the origin of the virus. This Trojan masks itself as a popular and common app and can stay undetected for a long time.
Another current threat is Gustuff, a Trojan targeting financial operations.[6] It has already intercepted more than 100 various banking apps. But it harms not only them. This malware also steals data from cryptocurrency applications, eCommerce platforms, and different payment services (PayPal, Western Union). It masks itself in a link from a text message. As soon as a person opens it and downloads a file, it gets access to the contacts. And all these contacts get such messages too. This malware is made to infect as many devices as possible.
Of course, these are just some examples with modest info. Check out our previous research on the Banking Malware & Attack Vectors Outlook research (Part 1 & Part 2) for more details.
And our Mobile Banking Threats Webinar in which our team takes a deep dive into the mobile banking malware.
Is Mobile Banking Safe to Use?
So the reasonable question one might have is: is mobile banking safe to use? After all, there are lots of threats online. The answer is yes, generally it is safe to use as every bank has a cybersecurity team that makes sure the app itself has all types of protection.
But the fact that it is mostly safe doesn’t mean that it is completely risk-free. The main problem with malware is that it is constantly evolving. A top-notch cybersecurity professional needs to be aware of that and proactive in problem-solving. And even that doesn’t guarantee 100% of success simply because nothing does. With any type of protection, there is a risk that malware will evolve faster.
The problem usually doesn’t originate from the banking solutions but the mobile devices themselves. And just because we use them so much— 51% of time online is spent on mobile devices compared to 42% of desktop usage (7% goes to other tools).[7]
In general, regardless of the device, the users should only install apps from verified mobile app stores. But that isn’t also entirely risk-free. Mobile app stores cannot deal with the number of fake applications with malware. Simply because there are too many of them. Both Google and Apple haven’t been able to prevent the publishing of such software.
Malware is one of the main risks to mobile banking.
Ultimately, every person is responsible for what they download, but businesses are responsible for providing the most advanced security measures.
It is safe to say that malware is one of the main threats mobile banking has to meet. It is widespread, it easily infects many devices, and it is constantly evolving. One Trojan can affect a hundred different apps, which makes it a common problem for all institutions in the industry.
One might say that if a user downloads malicious software, it is their responsibility. But it is not the case with banking. Security of personal finances is the bank’s prime focus. The banks should take all the measures to protect their clients. Otherwise, they risk losing reputation and customers.
After all, banking is hugely built on trust and credibility. No one wants to trust their money to someone who cannot guarantee its safety.
How can users & banks protect from mobile malware
Preventing mobile banking malware from inflicting any damage can be done from the user’s perspective and the bank’s perspective.
The users have a big responsibility when it comes to the security of their devices. To prevent malware from infecting their devices users should:
- Browse on safe and trusted websites
- Be mindful of what apps you’re installing on their mobile
- Install apps only from trusted sources
- Install a good anti-virus software
- Update all software regularly
Conversely, users should not install all apps they see nor visit shady websites.
On the other hand, banks can do a lot to minimize the impact of malware on their business.
Banks can have specific divisions or dedicated personnel that can develop processes that will minimize the risk and exposure. As well as dedicated teams that will work together with their clients on ensuring secured and malware-free devices. Additionally, banks can engage with cybersecurity consultants for further protective measures for both internal and external systems.[8]
Additionally, banks can use advanced technologies, such as ThreatMark, to detect malware installation on specific devices and prevent it from inflicting any damage.
ThreatMark successfully detects online banking threats across devices. Discover ThreatMark’s threat detection scope in the datasheet, here.
Conclusion
Mobile malware is one of the main concerns for mobile banking. There is a wide range of malicious apps collecting personal data, logins, and passwords to steal money and compromise security systems.
They can quickly infect many devices because of the ingenious ways they exploit the overall vulnerability of mobile operating systems.
It is safe to say that no individual or organization is completely safe from such attacks. That’s why it is a primary concern for mobile banking, but also all other industries, is dealing with sensitive data.
As the number of threats grows every year, it is crucial to stay on top of the problem and educate users about active threats, as well as, upgrade protection measures accordingly.
ThreatMark can help banks detect devices with active malware and a way to react to that intelligence.
This article has been produced in partnership with Mobilunity—a nearshoring company that provides dedicated development teams for businesses all around the globe. Visit Mobilunity at https://mobilunity.com/.
[1] CheckPoint, Check Point’s 2021 Cyber Security Report Reveals Extent of Global Cyber Pandemic, and Shows How Organizations Can Develop Immunity, https://pages.checkpoint.com/cyber-security-report-2021.html [last accessed: 25.05.2021]
[2] McAfee, McAfee Labs Threats Report 04.21, https://www.mcafee.com/enterprise/en-us/assets/reports/rp-quarterly-threats-apr-2021.pdf [last accessed 25.05.2021]
[3] Avast, How smartphones have become one of the largest attack surfaces, https://blog.avast.com/smartphones-and-increasing-mobile-threats-avast [last accesseed: 25.05.2021]
[4] CNET, Zeus botnet steals $47M from European bank customers, https://www.cnet.com/news/zeus-botnet-steals-47m-from-european-bank-customers/ [last accessed: 25.05.2021]
[5] FireEye, SlemBunk: An Evolving Android Trojan Family Targeting Users of Worldwide Banking Apps, https://www.fireeye.com/blog/threat-research/2015/12/slembunk_an_evolvin.html [last accessed: 25.05.2021]
[6] CryptoMathic, Protecting Banking Apps Against Malware Threats, https://www.cryptomathic.com/news-events/blog/protecting-banking-apps-against-malware-threats-1 [last accessed: 25.05.2021]
[7] Security Intelligence, Is Mobile Banking Safe?, https://securityintelligence.com/is-mobile-banking-safe/ [last accessed: 25.05.2021]
[8] Mobilunity, 5 Important Reasons to Hire Cyber Security Consultants, https://mobilunity.com/blog/cyber-security-consultants/?utm_source=0421_5005 [last accessed: 25.05.2021]

