StrandHogg Opens Doors to Financial Fraud, Circumventing Android’s Security Measures
Another powerful weapon lays in the hands of fraudsters. A dangerous Android vulnerability dubbed StrandHogg allows a malicious application to pose as a legitimate one for malicious purposes. Unlike a legitimate application, however, the sole goal of the StrandHogg malware is to wreak havoc by stealing credentials, recording phone calls or stealing the personal data located on users’ devices. But how does it work?
The Harmful Potential of StrandHogg
StrandHogg comes from the old Norse term, describing war tactics utilized by the Vikings. And just like during the Viking Age, no one is safe. All versions of Android are affected, and the full devastating potential of the malware can be unlocked even without having your phone being rooted. The StrandHogg malware is capable of causing significant damage even without a user granting the malicious application any additional special permissions.
The use cases for StrandHogg malware applications are vast. The attackers can gain access to the personal files of a user and use these for blackmail purposes; they can record phone calls, gain access to the device’s camera, or gain access to the contact list. How does this relate to financial malware? A fraudster’s ultimate goal is to gain access to the victim’s banking application, in order to siphon the funds into their account. This is obtained by first stealing the credentials, and secondly, stealing the step-up authentication code, in most cases, an SMS OTP (one type password). StrandHogg’s unique capabilities allow the malicious application to do both, with very little efford.
Firstly, a user must download the malicious application. The malware masquerades itself as a legitimate application on the web, such as a weather app, waiting for an unsuspecting user to download it onto their device. Once the malware is installed, StrandHogg can exploit the Android vulnerability in order to gain unlawful access to the data stored on the device.
StrandHogg is able to draw an overlay layer without having the permission to do so. Utilizing the overlay attack, a user hands over their credentials to the fraudster through an invisible layer rendered over the legitimate application. Once the fraudster gains the credentials used for accessing the banking application, all they need is an access to the text messages to capture the SMS OTP sent by the bank.
Which is a breeze for StrandHogg. A victim is prompted by a legitimate application to grant an SMS reading/forwarding permission. The user is however not granting these to the legitimate application, rather to the StrandHogg malware hiding in the background. Once the permission is granted, the fraudster can read and forward all SMS messages to their device, gaining the SMS OTP bank sends as a second factor of authentication.
These two steps were enough to grant the fraudster an access to the users’ banking application, where they can now transfer the funds into the fraudsters account without the user’s knowledge. And this is not the end. There are other similar dangerous permissions that StrandHogg can utilize – just see the list below.

When you open a legitimate banking application, StrandHogg can ask you for any permission or phish your credentials directly.
What the Flaw!
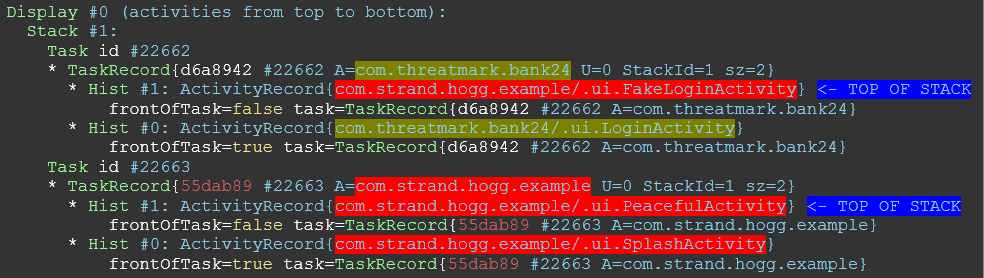
StrandHogg takes advantage of an Android multitasking flaw, allowing a malicious application to take over what is presented to the user and modify it. It is based on a configuration option called „taskAffinity“ which allows any application to „hijack“ other applications with its malicious content.
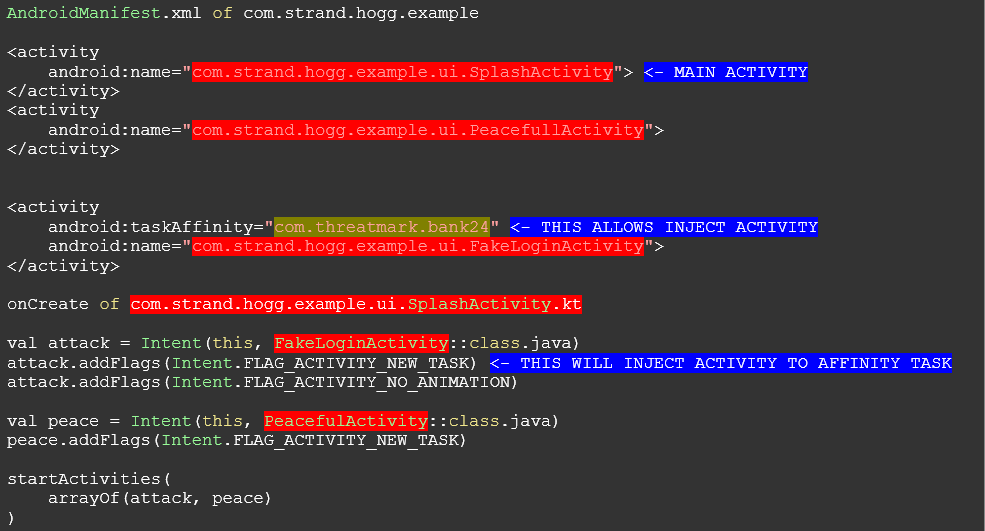
It has been confirmed that 36 malicious apps are already exploiting this vulnerability and as of now, 60 financial institutions have been targeted by some of these applications. But the full potential of StrandHogg malware has not been reached and the final damage might be unprecedented in terms of scale.
List of StrandHogg’s possible attack vectors include:
- Impersonate a legitimate app
- Use the device’s microphone and camera
- Read and send SMS messages
- Make and record phone calls, read their logs
- Steal credentials using an overlay attack
- Get all files on the device including contact list
- Get location data
How to Protect Yourself
Currently, it’s not easy to detect whether your device has been compromised by StrandHogg malware, but it is definitely possible. Nevertheless, well-informed users may notice a strange behavior while using their device, such as applications suddenly asking for login credentials, permission popups without reason or applications asking for inappropriate permissions. As usual, typos and graphical mistakes might reveal the fraud as well. As all instances of StrandHogg have been found on other sources than Google Play, it is crucial to check the source of the downloaded application. Always download applications from trusted sources to limit the potential of downloading a malicious application.
How does ThreatMark protects banks against vulnerabilities such has StrandHogg? Employing our Endpoint Protection Module which uses a dedicated SDK, ThreatMark performs multiple sophisticated checks to determine the credibility of any application installed on the device. ThreatMark utilizes known blacklists, checking the hash of each application against a proprietary database of known blacklisted malware. On top of that, ThreatMark analyses each application from the permission’s point of view, focusing on applications using SMS or Overlay permissions, whose combination stands often behind many vectors of attacks.
Moreover, ThreatMark SDK detects if some installed applications can exploit StrandHogg vulnerability against the protected application. Realtime application scanning can reveal potential problems quickly and, as a rule, earlier than can malware affect any user. This feature complements ThreatMark’s zero-day malware detection.
But this is only a small fragment of the ThreatMark’s holistic anti-fraud suite. The SDK protects the integrity of the banking application, protects the application from being reverse-engineered, repacked or run in debugger or emulator. All of this and more combined with an intelligence of over 15 million blacklisted apps provides a complex security solution, capable of detecting multiple sophisticated vectors of attack.
Would you like to learn more about our solution? Let’s discuss how ThreatMark can help your bank by leveraging a layered security approach in a combination with behavioral biometrics. Arrange a meeting with our experts and find a perfect fit for your use case.

