“Screen Records” Banking Apps to Steal Users Passwords – Upgraded Anubis & Bian Lian Android Malware
The lethal Banking Trojan known as the ‘Anubis’ made the headlines last year, for being Malware notoriously able to sneak into android gadgets, disguised under various, well-ranked downloads from the Google Play Store and stealing funds from thousands of Android users around the globe.
This week, the Android Banking Trojan has once again managed to bypass Google Play Store security measures and has returned with newly added features, which allows it to record the screens of infected devices while also adding new techniques that help the malware remain hidden from its victims.
Anubis is enabled by a ”dropper” with a proven ability to infiltrate Google Play and plant malicious downloaders under the pretense of innocent, benign-looking apps.
The new and ”improved” Bian Lian has changed its tactics and morphed into a sophisticated malware that bypasses safeguards on Google Play to reach its user base, bringing with it new techniques to the attack on banking apps, recording screens to steal credentials, locking out users to hide its activities and rendering devices unusable. Once Bian Lian has received permission to use a device’s accessibility services, the attack can begin. Financial windows can be recorded using a new screencast module as users type in usernames and passwords, card details and account numbers, sending all this sensitive information back to the cybercriminals behind the attack.
With the level of sophisticated Banking Malware and these types of attacks on the increase, businesses need a proactive approach to security that keeps pace with rapidly evolving threats and opportunities.
How can ThreatMark Assist
To stay on top of such attacks, ThreatMark uses the added protection of “Trusted User Identity” which is a robust combination of Threat-Detection Capabilities, Transaction Monitoring Analysis and Deep Behavioral Profiling of users. This holistic approach is key to detecting Zero-day attacks and recognizing in real-time, a legitimate bank account holder from an attacker.
With ThreatMark, you are able to detect and manage Mobile Banking Fraud and Cyber Threats sooner. Our solution is engineered in a unique way to provide multi-layered security for mobile and online channels by combining Deep Behavioral Profiling with powerful Threat Detection Engine, that gives you the visibility and awareness you need to take preventative action to avoid and minimize the impact of cyberattacks.
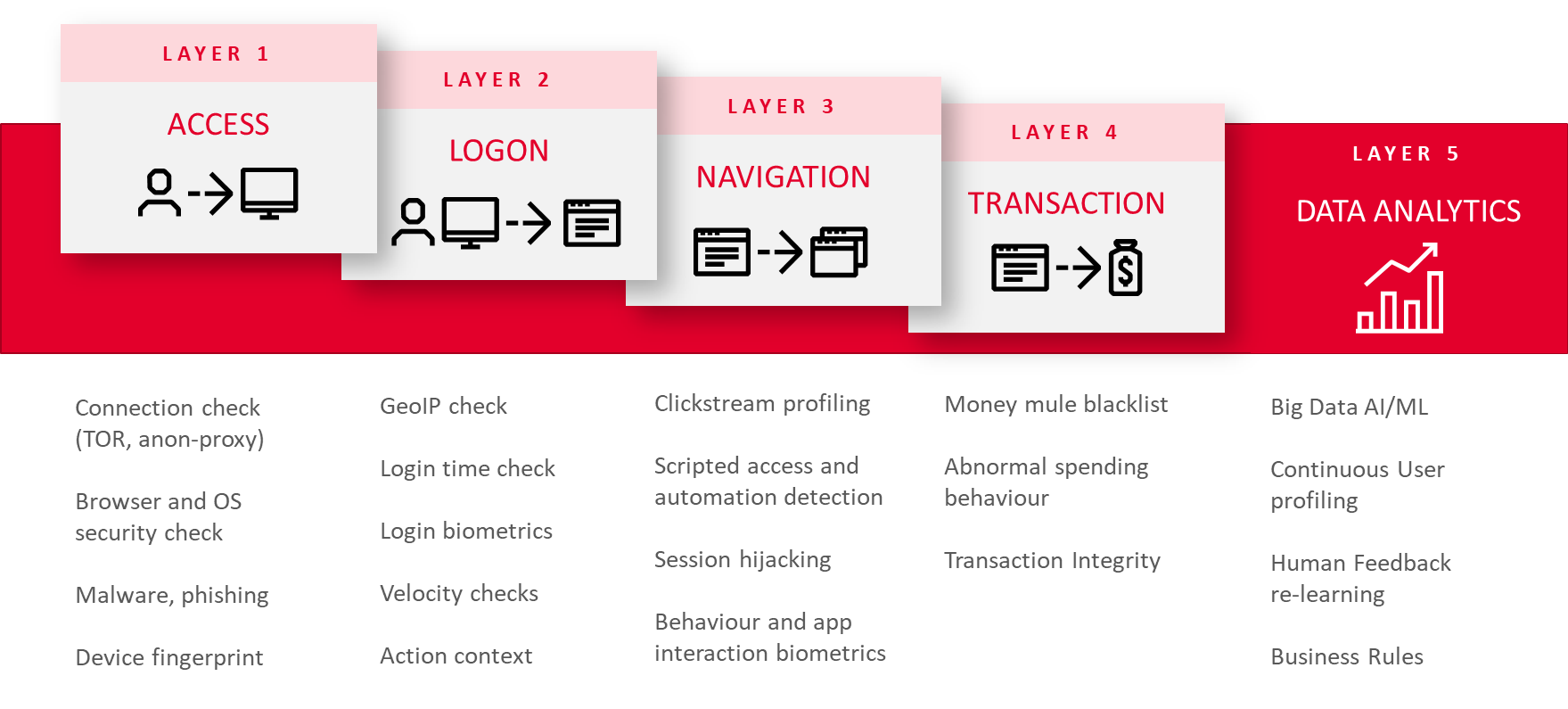
With Google’s continuous battle to police Google Play, to try ensure that malicious apps cannot get through its safeguards (GPP analyzes more than half a million applications every day) and based on the waves of recent malware campaigns, it indicates that there is still potential for improvement. Which is why we custom developed our SDK library to protect your clients’ end-points against various types of threats, such as overlay attacks, mTAN interceptions, keyloggers, SMS grabbers, Banking Trojans, mobile-based identity theft attacks, and cross-channel attacks.
Our SDK does not prevent any application from being installed but continuously scans them and the whole device from a security perspective, detecting and flagging compromised, rooted/jailbroken devices, insecure networks or malicious applications and tools being installed to further mitigate mobile-specific fraud and threats.
Feel free to contact the ThreatMark Team should you require any further information regarding Mobile Banking Fraud or if you would like a quick demonstration of our Anti-Fraud and Threat Detection Solution.

